Automation is a critical component of digital transformation, in that it is the automation of tasks via applications that is the focus of the first phase of the business journey known as digital transformation.
Automation of workflows consumes mindshare in the second phase as business expands its digital presence to create experiences.
And automation is central to the creation and subsequent use of actionable insights through AIOps and other AI-driven technologies in the third and final phase, AI-Assisted Business.
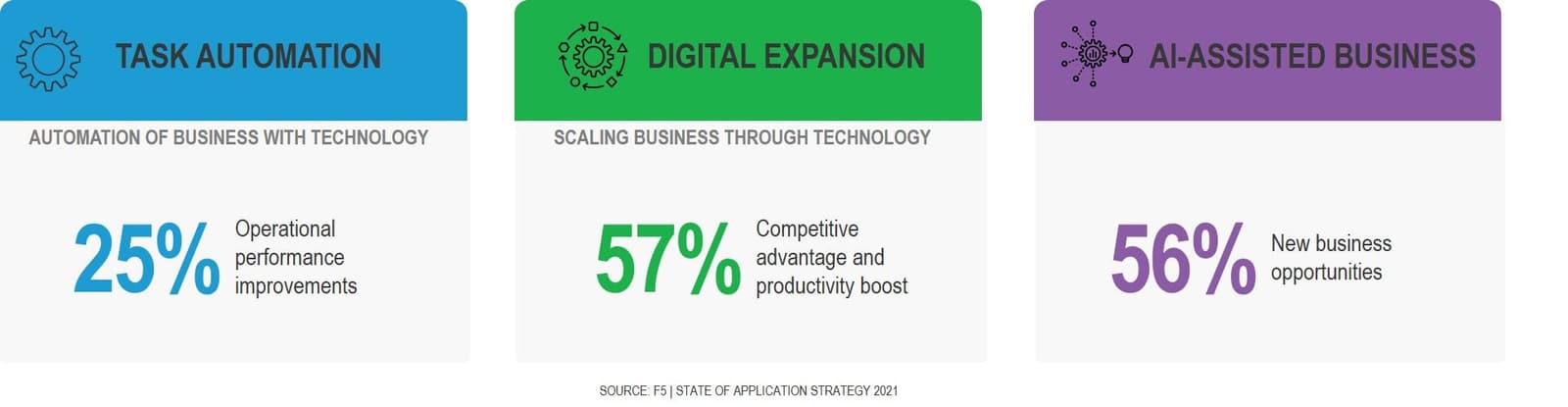
Automation is such a key concept it’s hard to talk about it without some context describing what it is we’re automating.
When Cindy Borovick and I sit down every year to hash out what we want to learn from the State of Application Strategy, we try to craft questions that are relevant not just now but also provide a glimpse of what will be relevant in the future.
For automation, that means going beyond a basic understanding of the tools and technologies in use to implement automation. It means exploring how automation impacts operations and the business, as well as what’s challenging or frustrating to practitioners today. It also means understanding what approaches the market is adopting to move forward with automation and how those approaches are—or perhaps aren’t—having an impact on digital transformation.
One of those approaches is infrastructure as code.
Infrastructure as Code
Infrastructure as Code (IaC) is a practice adopted from DevOps and SRE methodologies that treat provisioning and configuration artifacts (files) in the same way developers treat code. That means it is ideally reviewed, tested, and versioned in a repository. This enables automation of the deployment pipeline because both people and tools can always refer to the latest artifact when they need to deploy a new instance of X (where X might be a web server or an API gateway or ingress controller or… you get the picture). In deference, perhaps, to its origins, the kind of automation enabled by IaC is often referred to as GitOps, because GitHub and GitLab are commonly used as the repositories of choice and both are well-integrated into pipeline automation tools today.
It turns out that organizations adopting IaC see benefits in terms of the success of automation efforts.
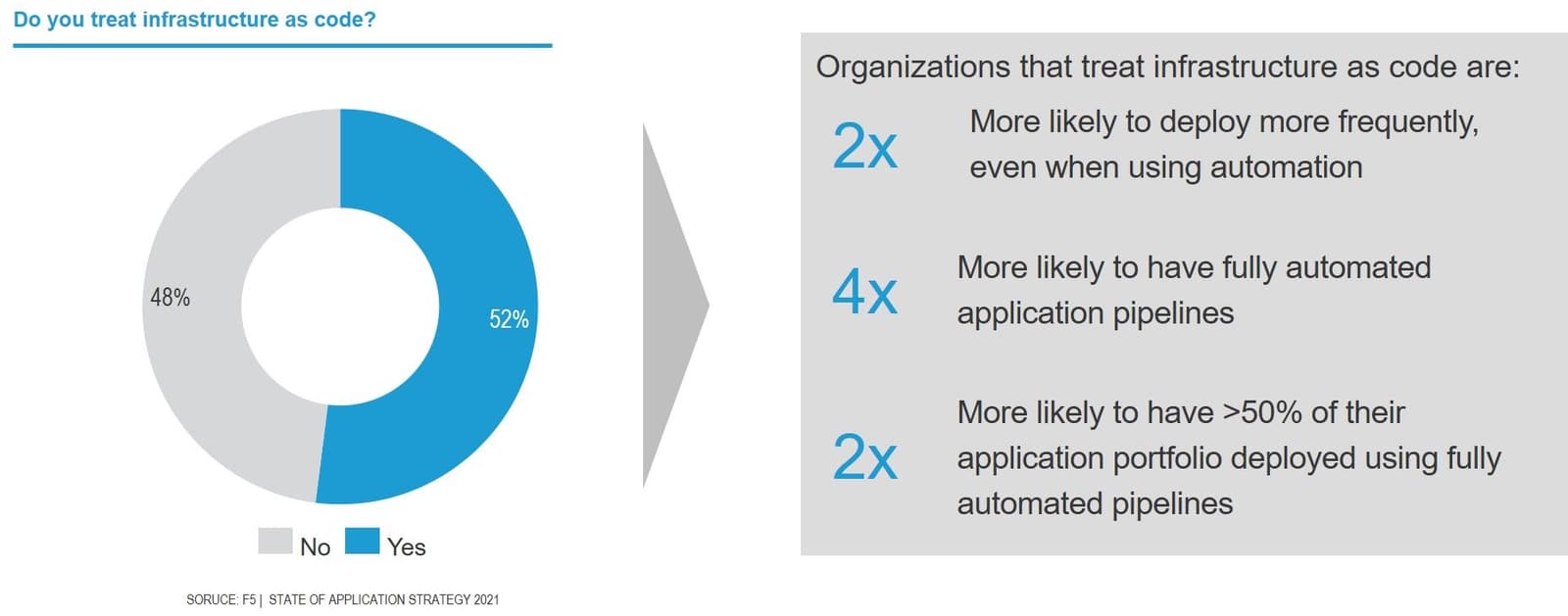
Just over half (52%) of organizations treat “infrastructure as code.” Those that do are more likely to deploy frequently, have fully automation-capable application deployment pipelines, and automate a larger percentage of their application portfolio than their contemporaries.
The benefits of IaC and automation are clear, so you have to wonder why more organizations aren’t adopting these approaches? It turns out, there are reasons, and those reasons are good ones.
Skills and Tools Top Challenges for Automation
You can’t automate without tools, and we’ve been tracking those tools for years. Emerging at the head of the toolset pack are multi-cloud and often open source options like Terraform and Ansible. While cloud-provider APIs are still heavily in use, they are cloud-provider specific. That poses a significant challenge for operations across all IT domains (security, infrastructure, and network) when operating applications across cloud properties.
Thus, the rise in popularity of cloud-agnostic toolsets is no surprise. Nearly half of all respondents (47%) are using tools like Terraform, Ansible, GitHub, GitLab, Puppet, and Chef. Coming in dead-last? Vendor-specific toolsets at just 29% of all respondents. That speaks to the need for comprehensive, cloud-agnostic automation because app portfolios and the technologies that deliver and secure them are now spread across multiple public and private clouds, data centers, and even the edge.
Toolsets are important because they are what enable organizations to treat infrastructure as code. The problem is that the number one challenge identified by respondents this year was skill sets, and the biggest gap in skill sets across the globe was … wait for it … toolsets.
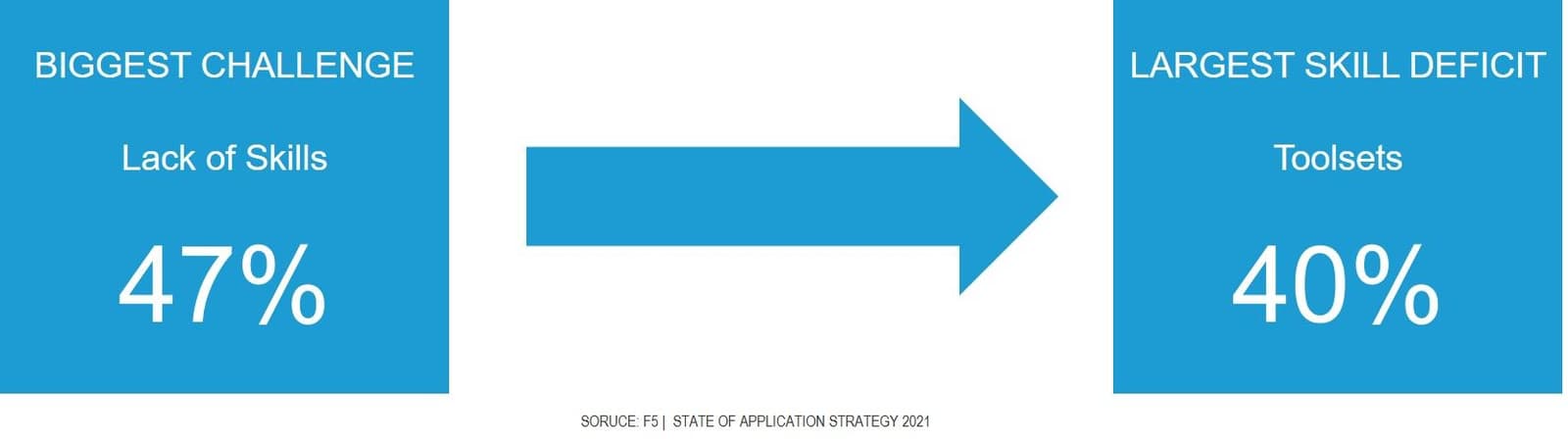
It is not difficult to conclude that to close the skills gap and enable more organizations to enjoy the benefits of treating infrastructure as code, we need to make toolsets easier to use, especially when it comes to cross-environment automation.
There are more insights on automation—and a whole lot more—in our annual report. Give it a read and then check back here as we unpack the current and future state of application security and delivery technologies.
About the Author

Related Blog Posts

Why sub-optimal application delivery architecture costs more than you think
Discover the hidden performance, security, and operational costs of sub‑optimal application delivery—and how modern architectures address them.

Keyfactor + F5: Integrating digital trust in the F5 platform
By integrating digital trust solutions into F5 ADSP, Keyfactor and F5 redefine how organizations protect and deliver digital services at enterprise scale.

Architecting for AI: Secure, scalable, multicloud
Operationalize AI-era multicloud with F5 and Equinix. Explore scalable solutions for secure data flows, uniform policies, and governance across dynamic cloud environments.

Nutanix and F5 expand successful partnership to Kubernetes
Nutanix and F5 have a shared vision of simplifying IT management. The two are joining forces for a Kubernetes service that is backed by F5 NGINX Plus.

AppViewX + F5: Automating and orchestrating app delivery
As an F5 ADSP Select partner, AppViewX works with F5 to deliver a centralized orchestration solution to manage app services across distributed environments.
F5 NGINX Gateway Fabric is a certified solution for Red Hat OpenShift
F5 collaborates with Red Hat to deliver a solution that combines the high-performance app delivery of F5 NGINX with Red Hat OpenShift’s enterprise Kubernetes capabilities.
