Compare F5 Distributed Cloud Services
Available on annual enterprise subscription, Private Offers in the major cloud marketplaces and Pay as you Go in AWS Marketplace.
Fill out this form to be contacted by F5 about Distributed Cloud.
Available on annual enterprise subscription, Private Offers in the major cloud marketplaces and Pay as you Go in AWS Marketplace.
Fill out this form to be contacted by F5 about Distributed Cloud.
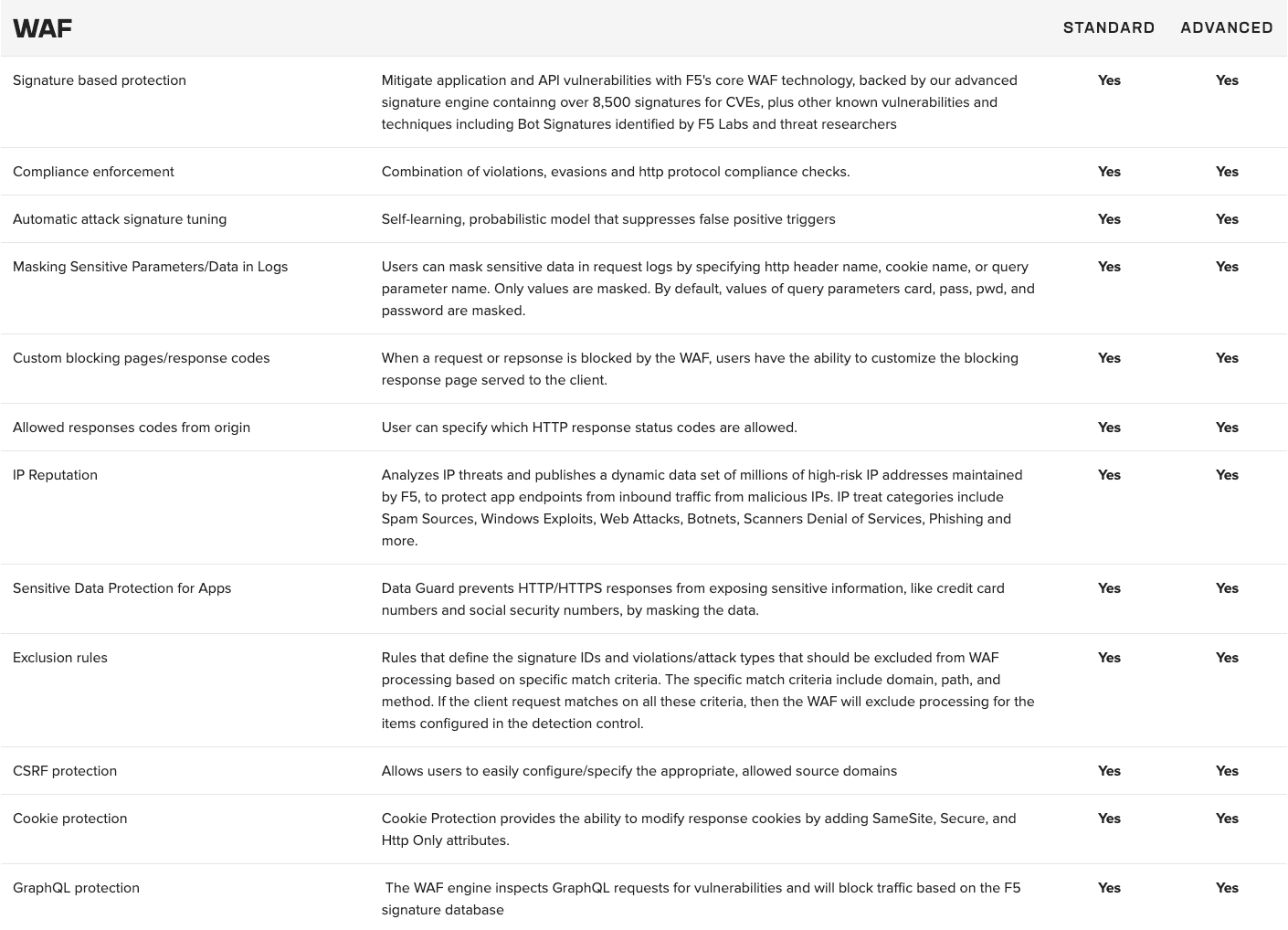
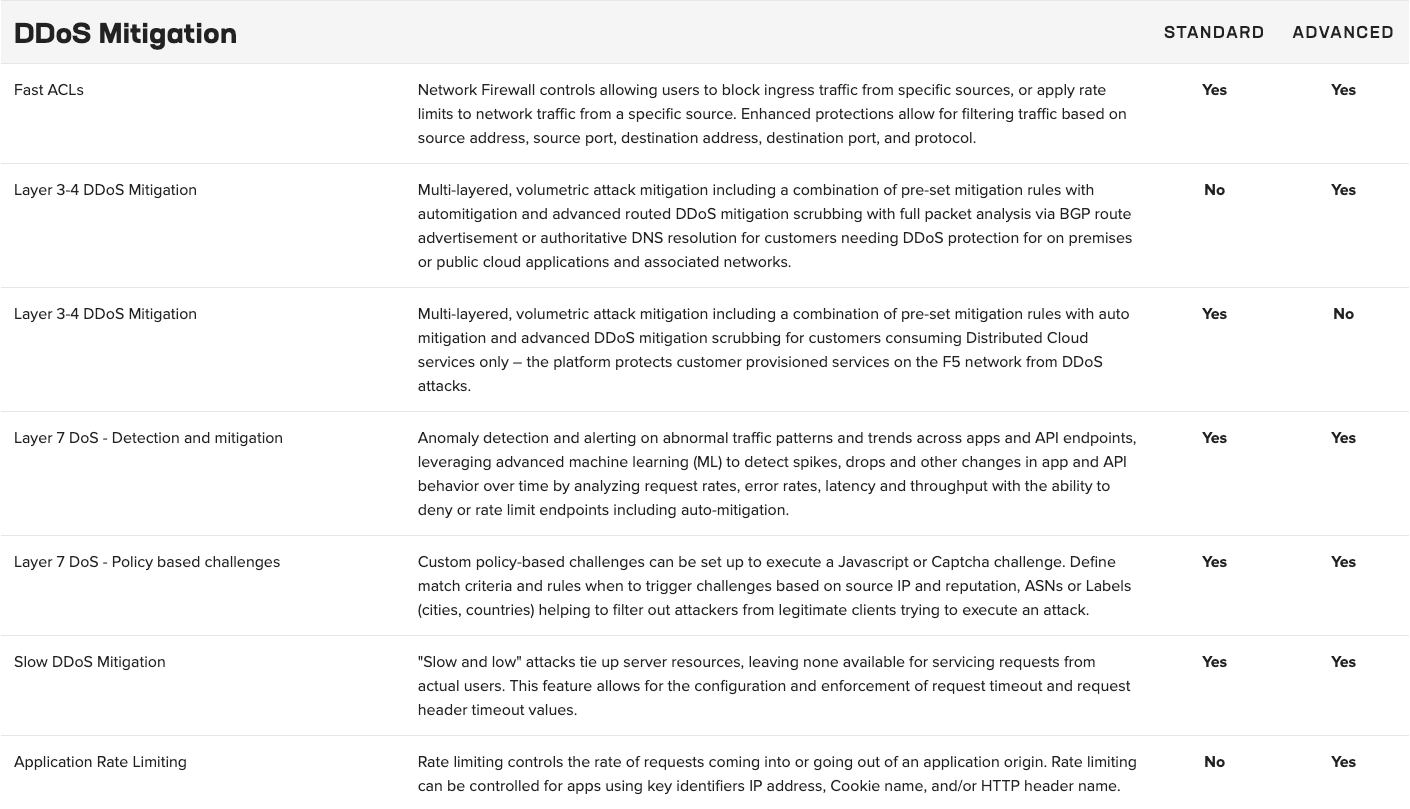
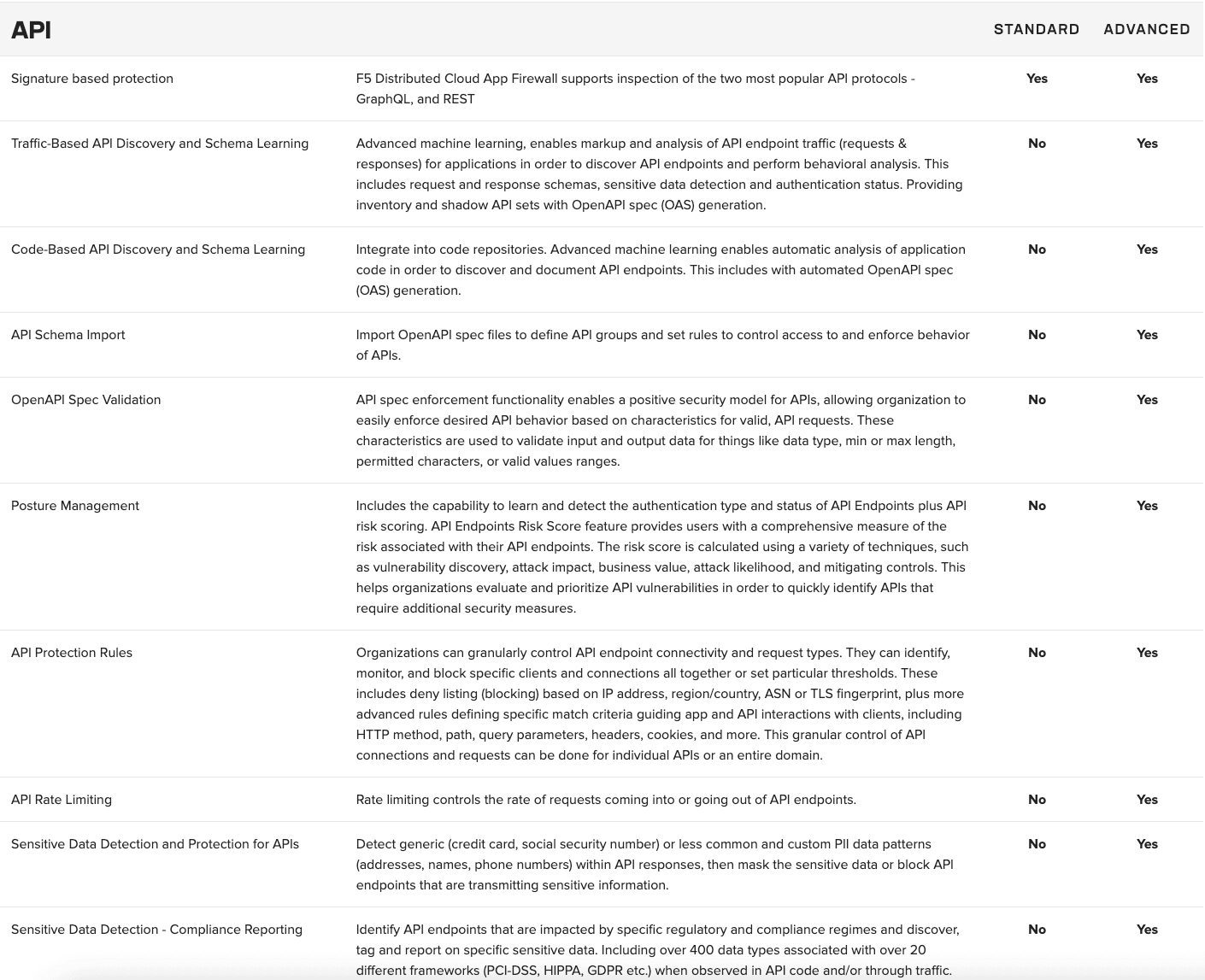
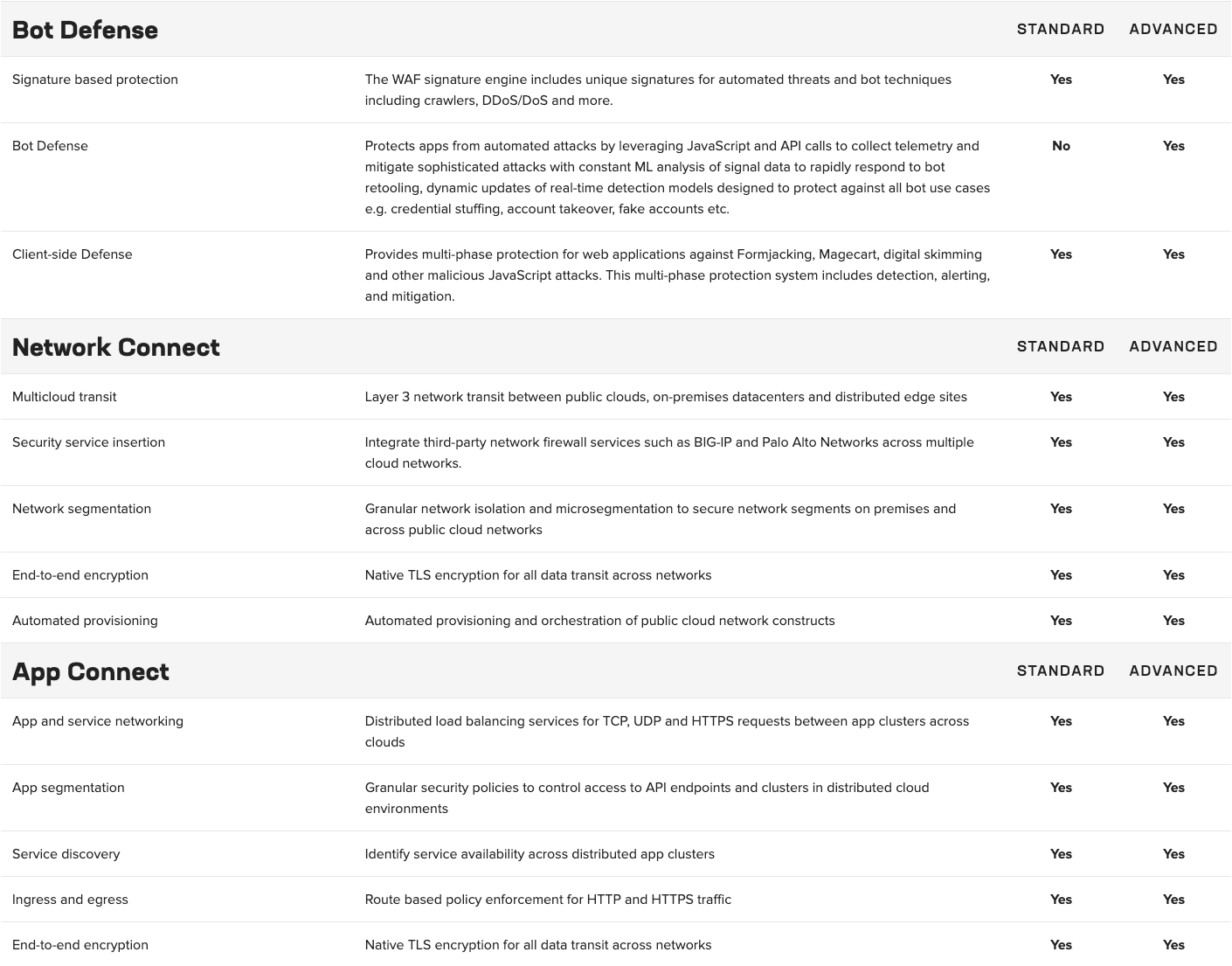
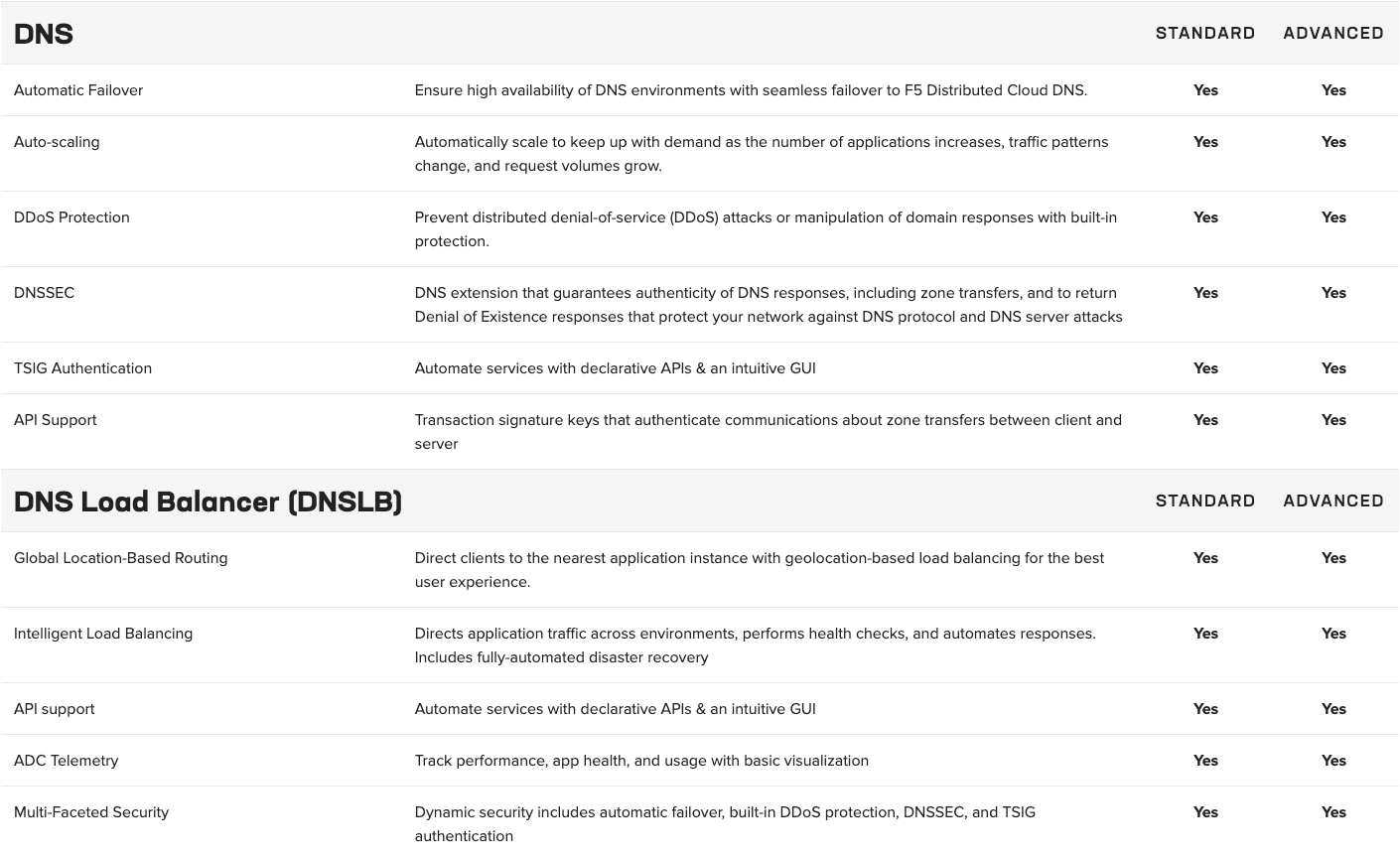
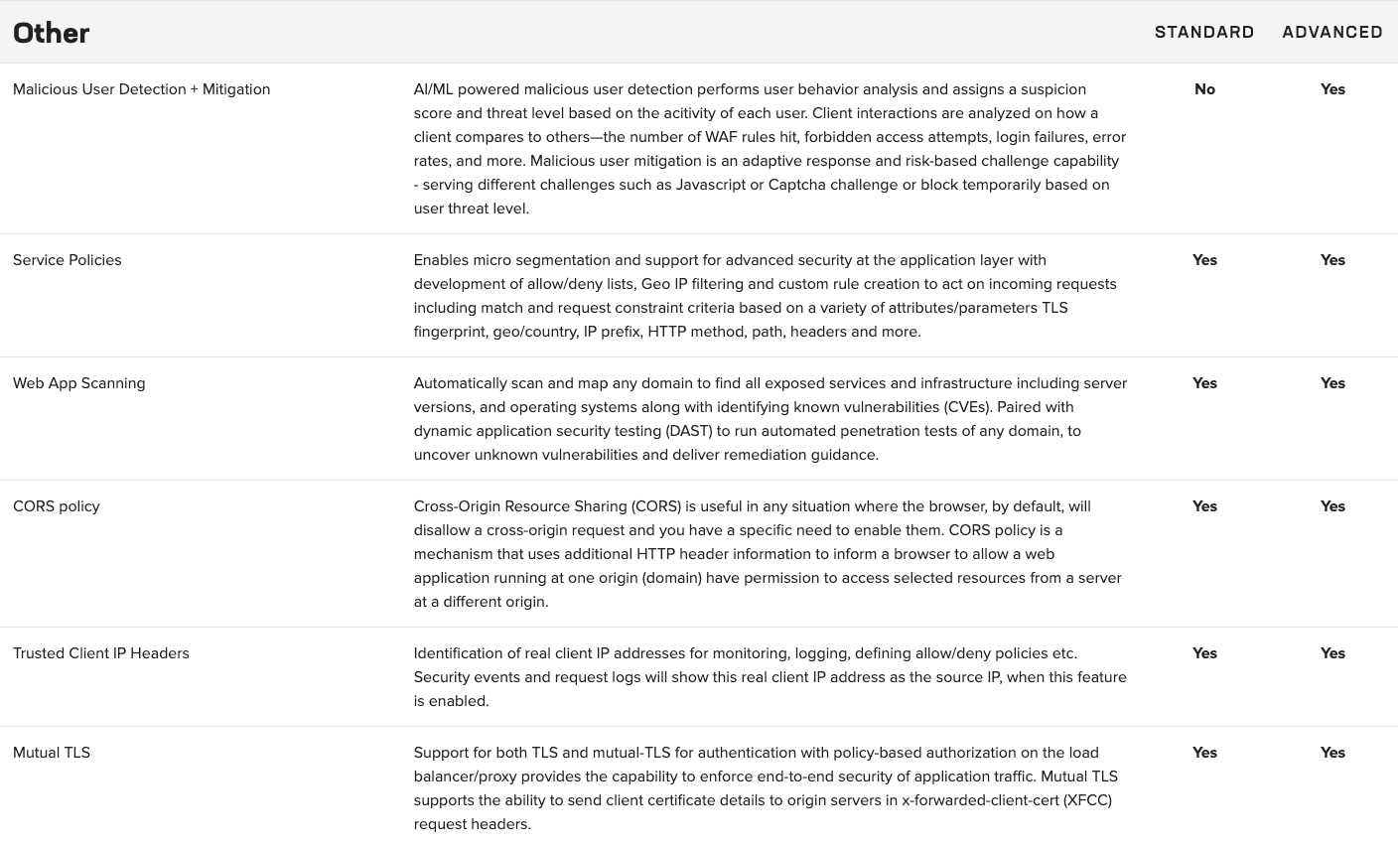
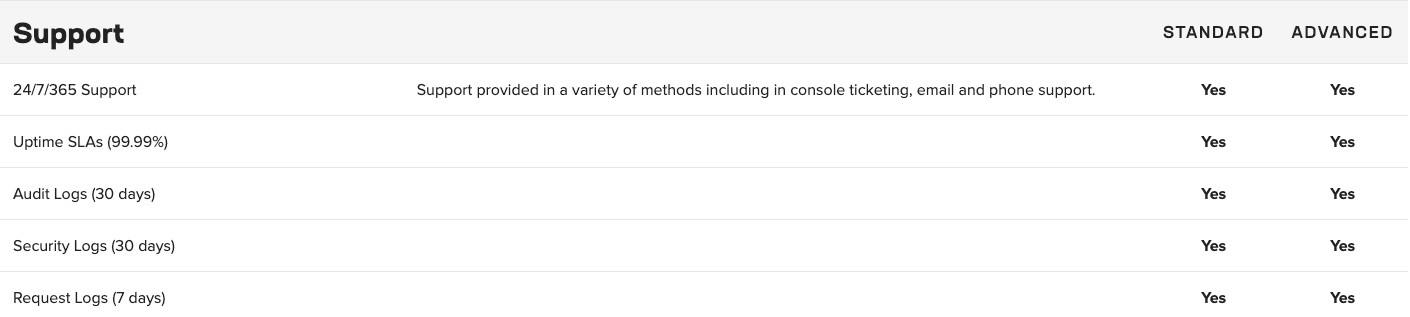
An annual subscription supports various use cases, including application security and multicloud networking. The Standard offerings provide basic functionality and service networking, while the Advanced offerings are specifically designed to meet stringent requirements for advanced API security across distributed cloud and edge sites.
Compare Standard and Advanced ›
Advanced application security includes API discovery and protection, behavioral bot mitigation, and Layer 7 DDoS mitigation.
Extend hybrid and multicloud networking to support advanced use cases for secure service networking between distributed application clusters across multiple clouds, on-premises, and edge sites.
Improve global application performance and reliability with CDN, DNS, and App Stack.