使用 Cisco Firepower Threat Defense 和 F5 SSL Orchestrator 进行事件补救
F5 SSL Orchestrator 可帮助公司保护其企业安全,并提供必要的规模以防止各种攻击类型、载体和表现形式,同时提供对穿越不同安全区域的数据流量的毫不妥协的可视性。 与强大的分布式拒绝服务 (DDoS) 策略相结合时,SSL Orchestrator 及其与 Cisco Firepower Threat Defense (FTD) 的集成可提供外围安全的必要组件,并通过保护企业免受恶意软件、机器人和其他攻击来提供全面保护。
为了实现无缝集成,F5 与思科合作验证并制作用于集成 SSL Orchestrator 和 Firepower Threat Defense 的参考架构。 测试和验证在 F5 实验室设施中使用带有 FTD 的虚拟和物理 Firepower 设备进行。
本指南可帮助管理员识别和部署常见用例的经过验证的配置。 这里定义的客户场景解决基于策略的流量控制和阻止以及 SSL 可见性和控制。
该场景采用 SSL Orchestrator 根据负载将流量分配到不同的资源。 或者,使用商业智能进行分配,基于集中策略管理或 F5 iRules 等功能进行更深入的决策过程,FTD 资源可以利用这些功能进行检查。 例如,可以将applicationA 定向到具有专门规则集的一个 FTD 服务器池,该规则集监控特定于其环境的签名,而将applicationB 定向到另一个池。 与 Firepower 修复 API 的集成允许系统通过使用 iRule 将 IP 地址填充到阻止列表中来动态地做出反应以减少对 FTD 基础设施的需求。 在预设的一段时间内,已识别违规者的流量在进入 FTD 之前会被阻止。 由于攻击者的一种策略是提供大量分散注意力的流量来掩盖真正的攻击,因此这种补救策略可以让 FTD 集中资源来识别新的攻击,而不必补救已经识别的攻击者。
SSL 终止是一个资源密集型的过程,但 F5 设备包含专门用于 SSL 处理的专用硬件处理器。 对于入站和出站部署场景,利用 SSL Orchestrator 和 FTD 可以提供对 SSL 流量的毫不妥协的可视性。
在部署入站应用时,很少不考虑高可用性,而 F5 BIG-IP 实例上的 SSL 终止可确保安全且增强的应用交付,同时为 FTD 传感器提供对 SSL 流量的可见性。 根据安全策略规定,流量可以在传递到后端服务器之前重新加密。
现在使用 SSL 加密来保护用户的网站越来越多,这对 FTD 传感器池消除恶意软件和攻击的任务提出了挑战。 SSL Orchestrator 可以提供用户流量的全面可见性。
SSL Orchestrator 支持入站 SSL/TLS 检查,以防止加密威胁未被发现并危及关键资产。 通过消除安全盲点和阻止隐藏的威胁来保护您的应用程序和服务器。
经过验证的架构包含 Firepower 设备前端 Web应用服务器池的负载平衡池。 这种方法最大限度地提高了 Cisco 和 F5 组合解决方案的有效性,同时解决了 SSL 可视性和控制以及流量管理和阻止问题。 检查区域流量经过足够长的解密时间才能由 Firepower 设备检查,并在发送到应用服务器或客户端之前重新加密。
在图 1 中,Firepower 服务检查、阻止和报告所有网络流。 流量穿过 FTD 设备后,会通过 SSL Orchestrator 路由回来。 这确保可以检查流量,并且在必要时可以阻止 IP 地址。
图 1: SSL Orchestrator 创建了一个检查区,FTD 可以在其中检查流量并检测和阻止威胁。
SSL Orchestrator 支持出站 SSL/TLS 检查,以阻止恶意软件渗透到公司网络并防止通过加密通道进行命令和控制 (C&C) 通信。 该解决方案可阻止恶意软件感染、数据泄露和 C&C 通信。
经过验证的架构可保护内部客户端免受基于互联网的威胁。 客户端通过 SSL Orchestrator 访问互联网,SSL Orchestrator 解密此流量并将其副本发送到 Firepower 设备进行检查。
图 2: SSL Orchestrator 将出站流量发送到 FTD 进行检查,以保护内部客户端免受互联网威胁。
这些程序假设存在一个有效的 SSL Orchestrator 拓扑(无论是传入还是传出),并重点介绍添加 Cisco Firepower TAP 服务,包括以下步骤:
- 创建 Firepower TAP 服务。
- 创建 iRule。
- 创建虚拟服务器。
- 将 iRule 附加到虚拟服务器。
两种拓扑类型均受支持,并且思科补救解决方案的配置相同。 如果您尚未拥有可运行的 SSL Orchestrator 拓扑,请参阅F5 DevCentral 上的 SSL Orchestrator 文章系列,了解完整的配置步骤。
本指南概述了使用 SSL Orchestrator 部署 Cisco FTD 的必要步骤,包括 Firepower 服务(Firepower 节点)的配置、安全策略和 iRules 的应用。 FTD 可以部署为第 2/3 层或 TAP 解决方案。 SSL Orchestrator 可以部署为第 2 层或第 3 层解决方案。 SSL Orchestrator 提供了以最适合您的方式进行部署的灵活性。 例如,SSL Orchestrator 可以部署在第 2 层模式下,而 FTD 可以部署在第 3 层模式下,反之亦然。
熟悉 F5 部署概念和技术以及基本网络对于配置和部署 SSL Orchestrator 至关重要。 有关配置和网络设置的更多详细信息,请访问 F5 支持网站AskF5 。
尽管引导配置向导将帮助配置该解决方案的大部分内容,但仍有一些事情必须在其之外完成。 此示例使用现有的 L2 出站拓扑。
1. 在配置工具中,单击SSL Orchestrator > 配置 > 服务 > 添加。
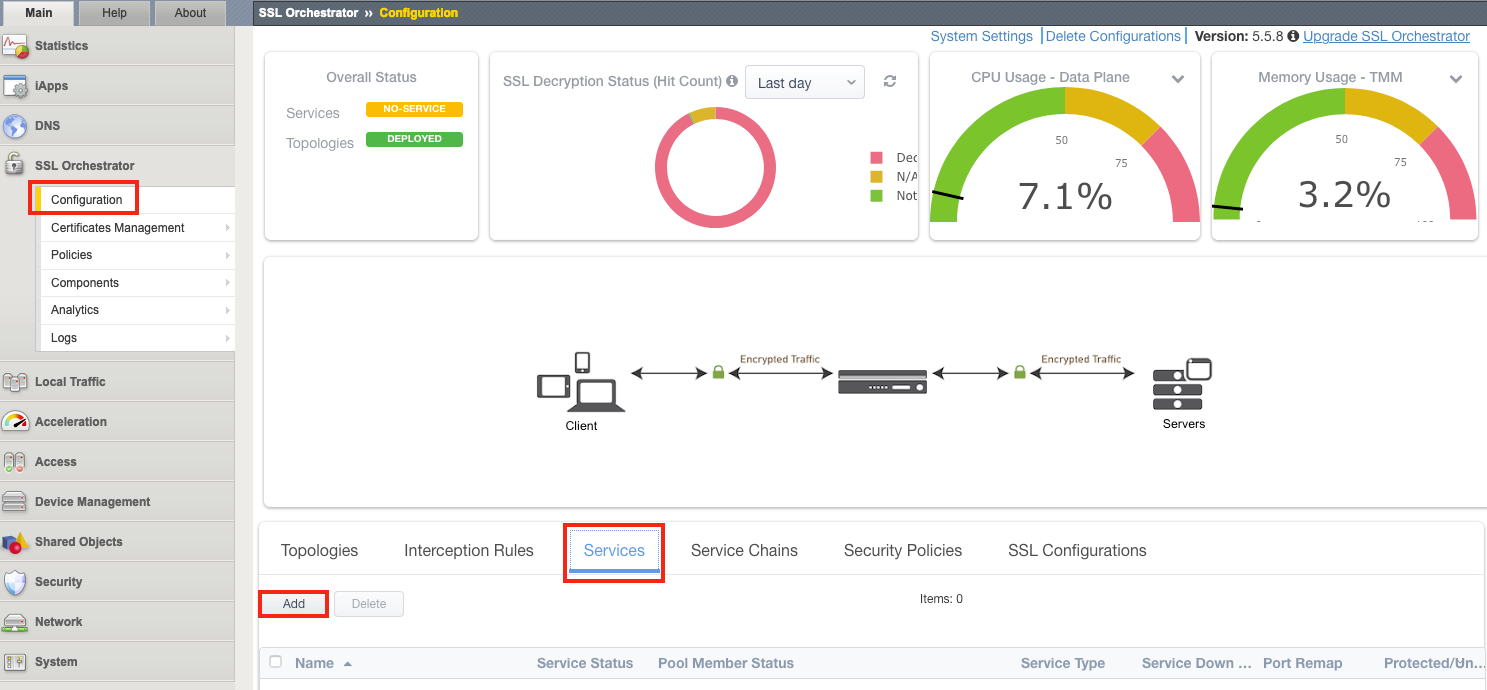
2. 在服务属性下,选择Cisco Firepower Threat Defense TAP并单击添加。
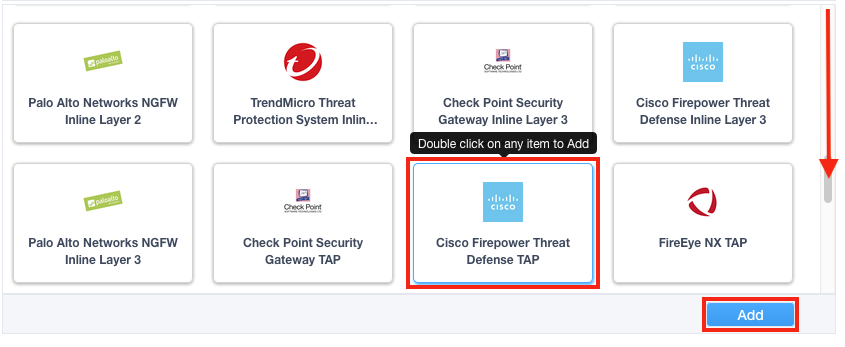
3. 命名服务并输入 Firepower MAC 地址(如果直接连接到 SSL Orchestrator,则输入 12:12:12:12:12:12)。
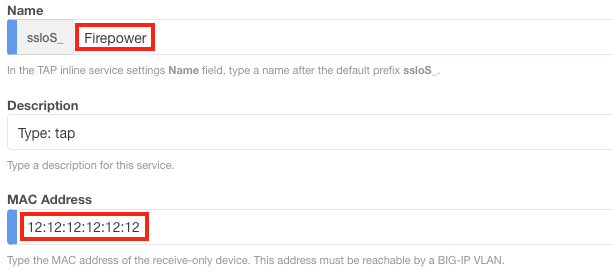
4. 在VLAN下,单击新建,输入名称(例如 Firepower),然后选择正确的接口(此示例中为 2.2)。 或者,如果您之前配置了 VLAN,请单击使用现有,然后从下拉菜单中选择适当的 VLAN。
笔记: 如果需要,指定 VLAN 标记。

5. 启用端口重映射是可选的。 单击“保存并下一步” 。
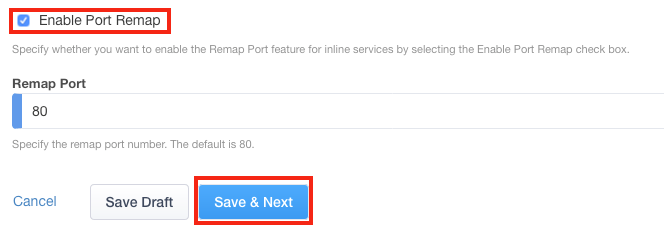
6. 单击您想要配置的服务链(本例中为 sslo_SC_ServiceChain)。 如果您没有现有的服务链,请立即添加一个。
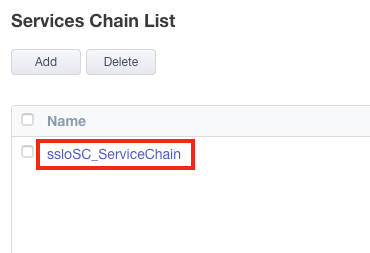
7. 选择 Firepower 服务并通过单击相应的箭头将其移动到“选定”列表。 单击“保存” 。
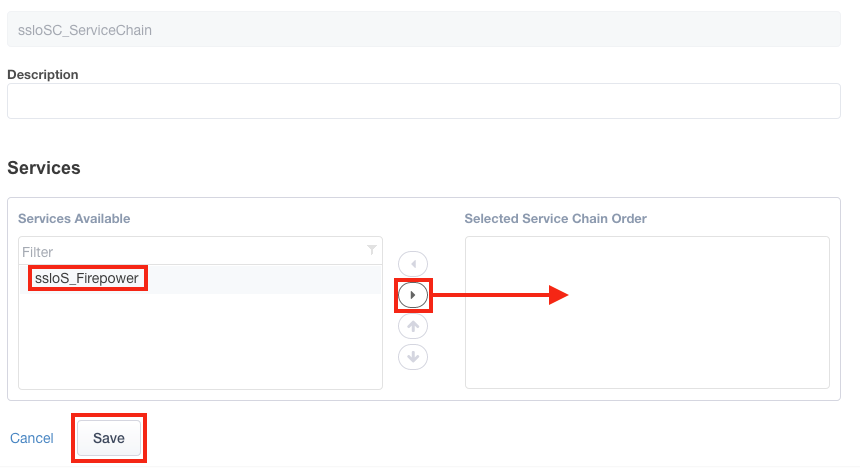
8. 单击“保存并下一步” ,然后单击“部署” 。
创建两个 iRule 和两个虚拟服务器。 第一个 iRule 监听来自 Firepower 设备的 HTTP 请求。 然后,Firepower 通过其补救 API 做出响应并发送包含 IP 地址和超时值的 HTTP 请求。 该地址是 SSL Orchestrator 要阻止的源 IP,它将在超时期限内阻止它。 有关详细信息和 iRules 教程,请查阅F5 DevCentral 。
1. 通过选择Local Traffic > iRules然后单击Create ,在 SSL Orchestrator 上创建第一个 iRule。
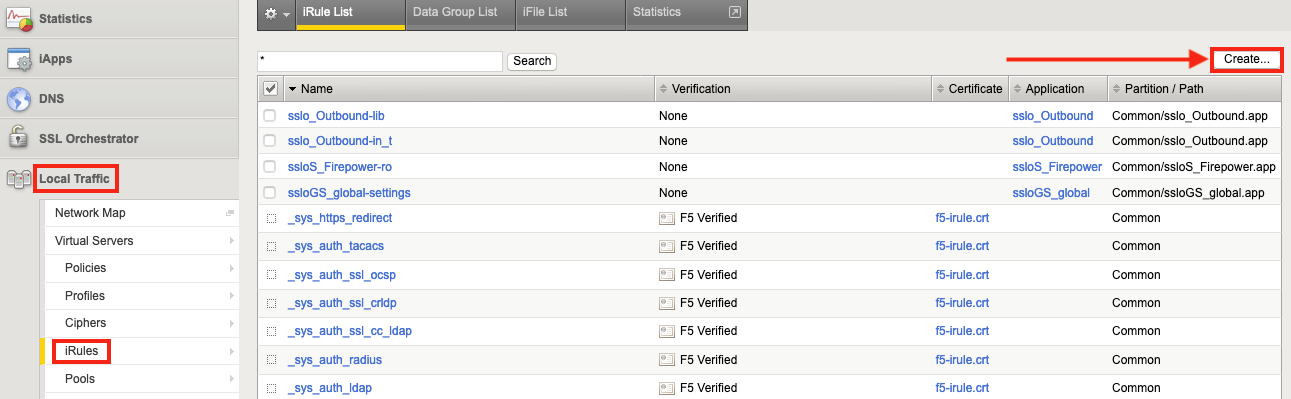
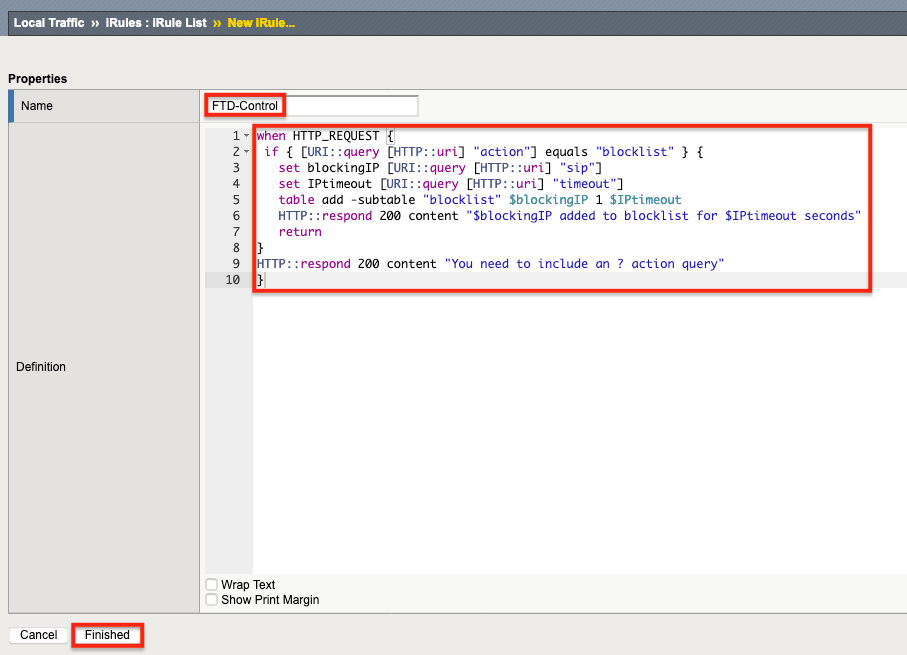
2. 命名 iRule(此示例中为 FTD-Control),然后将 iRule 的文本(如下图 3 所示)复制并粘贴到Definition字段中。 单击“完成” 。 此 iRule 将与控制虚拟服务器相关联。
当 HTTP_REQUEST { 如果 { [URI::query [HTTP::uri] "action"] 等于 "blocklist" } { 设置blockingIP [URI::查询[HTTP::uri]“sip”] 设置 IPtimeout [URI::query [HTTP::uri] "超时"] 表添加-子表“blocklist”$blockingIP 1 $IPtimeout HTTP::respond 200 content “$blockingIP 已添加到阻止列表,持续时间为 $IPtimeout 秒” 返回 } HTTP::respond 200 content“您需要包含?操作查询” }
|
|---|
图 3: 第一个要复制和粘贴的 iRule 文本
3. 再次单击“创建”来创建第二个 iRule。
4. 命名第二个 iRule(本例中为 FTD-Protect),然后将下图 4 中的 iRule 文本复制/粘贴到定义字段中。
|
|---|
图4: 要复制和粘贴的第二个 iRule 文本
5. 单击“完成” 。 此 iRule 将与 Protect虚拟服务器相关联。

1. 通过选择本地流量 > 虚拟服务器并单击创建来创建虚拟服务器。
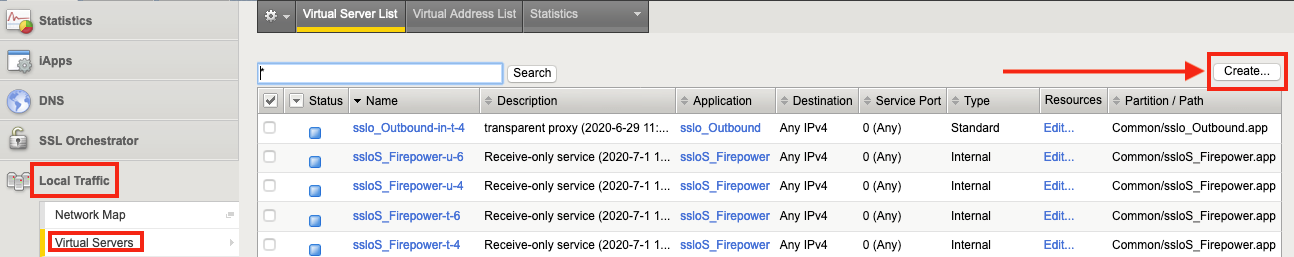
2. 命名虚拟服务器(记住关联 iRule 的名称)— 本例中为 FTD-Control。 对于类型,选择标准。
3. 对于源地址,输入 0.0.0.0/0,这表示任何源地址都会匹配。
4. 对于目标地址/掩码,输入 SSL Orchestrator 将监听的 IP 地址,以接受来自 Firepower 的 API 请求。 (在此示例中为 10.5.9.77/32,这表示 SSL Orchestrator 将只响应到该单个 IP 地址的连接。
笔记: 目标地址/掩码必须与 Firepower 管理中心上的第二个管理接口位于同一子网,这将在本指南后面讨论。
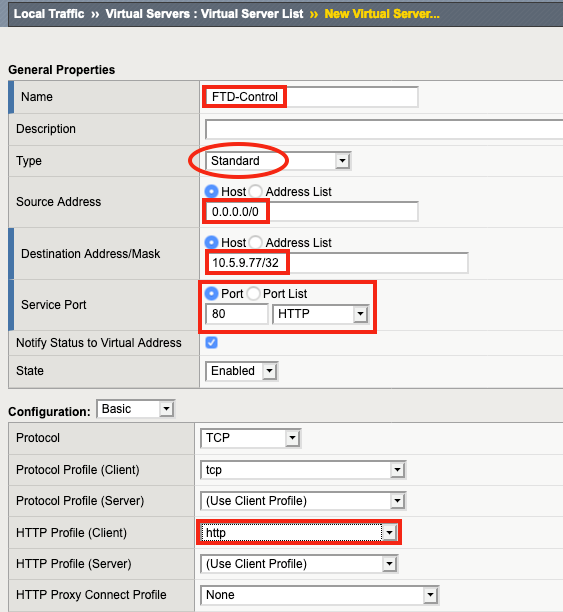
5. 对于VLAN 和隧道流量,F5 建议选择“在 Firepower 第二管理接口将使用的特定 VLAN上启用...”,而不是“所有 VLAN 和隧道” 。
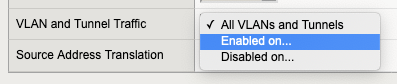
6. 选择 Firepower 第二个管理接口将使用的相同 VLAN(此示例中为 vlan509)。 单击<<将正确的 VLAN 移动到选定列表。

7. 在资源下,点击之前创建的 FTD-Control iRule,然后点击<< 将它移到已启用列表,最后点击完成。
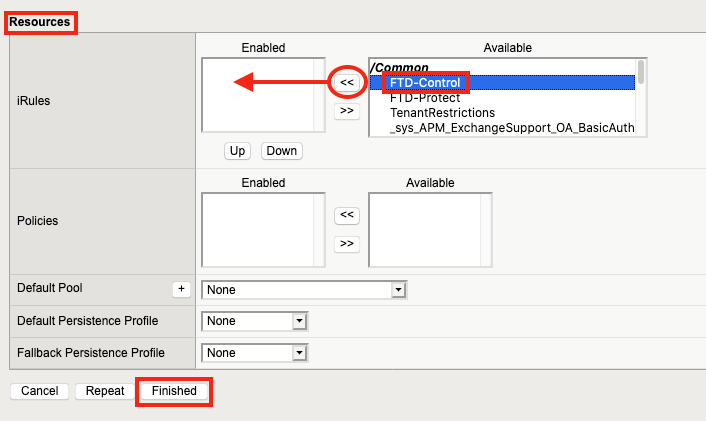
8. 要创建第二个虚拟服务器,请再次单击“创建” 。
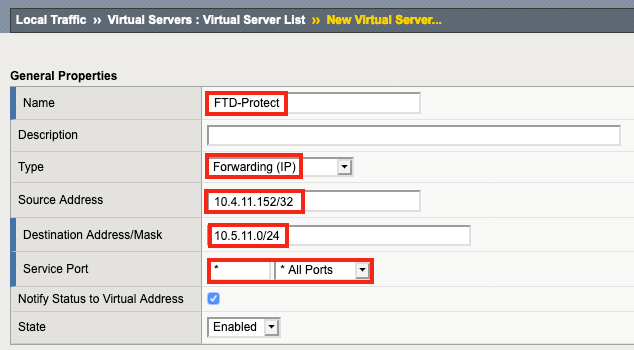
9. 命名虚拟服务器(此示例中为 FTD-Protect),然后单击“类型”中的“转发(IP)” 。
10. 输入源地址(本例中为 10.4.11.152/32)。 为了测试目的,该虚拟服务器将仅接受源 IP 为 10.4.11.152 的连接,以确保一切都能通过单个测试客户端正常运行。 对于入站拓扑,源地址可能设置为 0.0.0.0/0,这将允许来自任何地方的连接。
11. 输入目标地址/掩码。 在这种情况下,10.5.11.0 网络是 10.4.11.0 网络流量必须经过的目标,才能通过 SSL Orchestrator 并进入 Internet。
12. 在配置下,为VLAN 和隧道流量选择启用...。
13. 在可用下,选择 SSL Orchestrator 正在接收流量的入口 VLAN(此示例中为 Direct_all_vlan_511_2)。 单击<<将其移动到选定列表。

14. 在资源下,单击之前创建的 FTD-Protect iRule。 单击“<<”将其移至“已启用”列表,然后单击“完成” 。
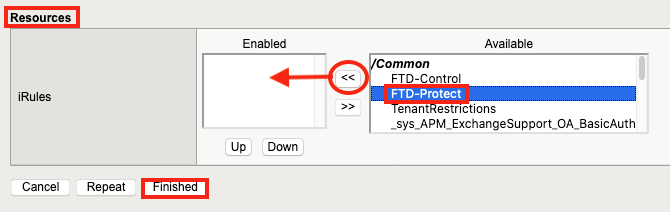
您现在拥有:
- 创建了 Firepower TAP 服务。
- 创建了 iRules。
- 创建虚拟服务器。
- 将 iRules 附加到虚拟服务器。
这些程序假定 Cisco Firepower 和 Firepower 管理中心 (FMC) 已获得许可和部署并且正常运行。
1. 登录 Firepower 管理中心以查看摘要仪表板。
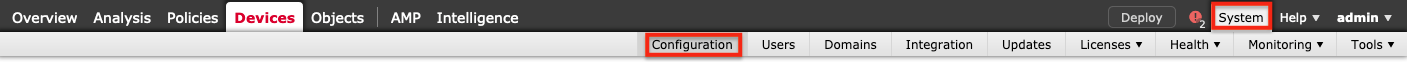
2. 单击系统 > 配置。 (将打开“设备”选项卡。)
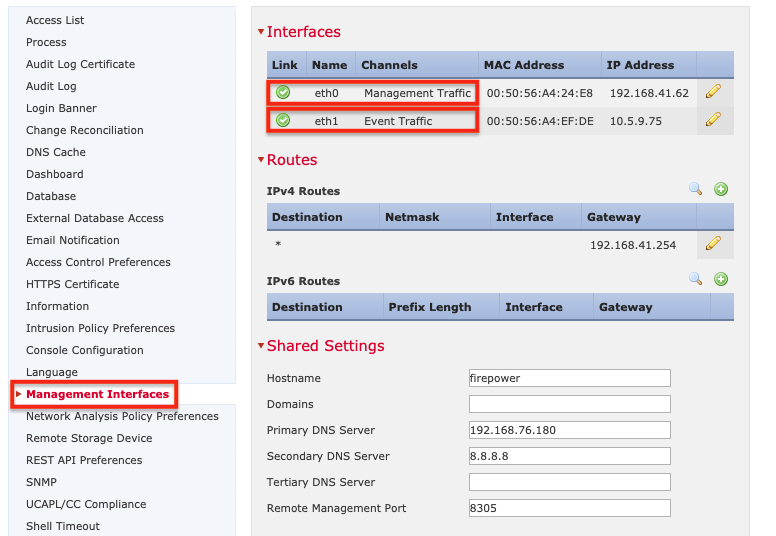
3. 单击左侧菜单中的“管理接口” 。 必须为事件流量配置 FMC 管理接口,并且必须与 SSL Orchestrator 上的控制虚拟服务器位于同一子网(示例中为 10.5.9.77)。
4. 当使用虚拟机进行 FMC 时,单击“添加新设备”并在虚拟机管理程序控制台中添加第二个 NIC。 (有关如何执行此操作的更多信息,请参阅下面的屏幕截图和您的 Hypervisor 管理指南。)

5. 要配置第二个管理接口,请单击铅笔(编辑)图标。
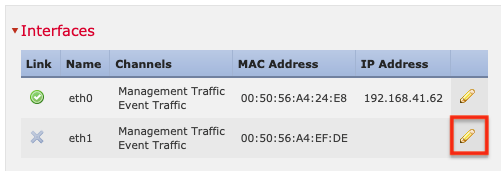
6. 选择已启用。 (必须启用事件流量,但不需要管理流量。)
7. 将IPv4 配置设置为静态。 输入IP地址和子网掩码,然后单击“确定” 。
笔记: 该接口必须与 SSL Orchestrator 上的控制接口位于同一 VLAN 和子网。

8. 单击“保存” 。
本指南假定 Firepower 设备已启用入侵和恶意软件策略(类似以下示例)。
接下来,创建 Firepower 补救策略。 补救策略可以根据几乎无限的一组标准采取各种行动。 例如,如果检测到入侵事件,Firepower 可以告诉 SSL Orchestrator 在一定时间内阻止源 IP。
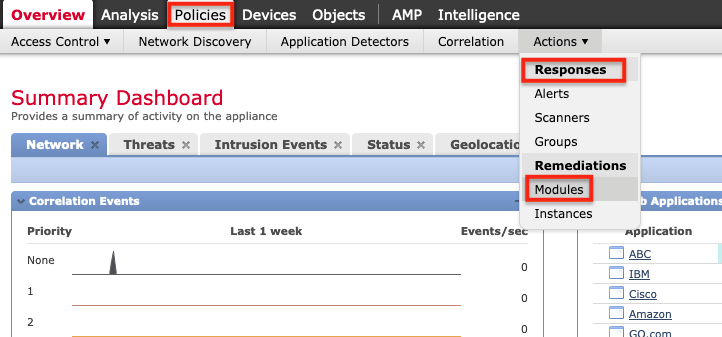
1. 安装 F5 补救模块。 为此,在 FMC 中,单击“策略”>“操作”>“响应”>“模块” 。

2. 单击“浏览”以找到计算机上的F5 补救模块。 选择它,单击打开,然后单击安装。 安装完成后,单击右侧的放大镜。
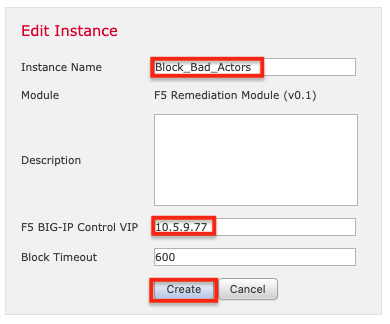
3. 单击“添加”以配置实例。

4. 命名实例(此示例中为 Block_Bad_Actors)。 输入 SSL Orchestrator 控制虚拟服务器的 IP 地址(本例中为 10.5.9.77)。 更改超时是可选的。 最后,点击创建。
5. 接下来,在“已配置的补救措施”下,单击“添加” 。

6. 将补救措施命名为(此示例中为 RemediateBlockIP),然后单击创建。

7. 选择“策略”>“关联”>“创建策略”来创建关联策略,该策略将定义何时以及如何启动补救措施。

8. 将关联策略命名为(此示例中为“补救”),然后单击“保存” 。

9. 在“规则管理”选项卡上,单击“创建规则” 。

10. 命名规则(此示例中为 RemediateRule)。

11. 对于事件类型,选择发生入侵事件。 (为了进行测试,还请参阅下一步中的注释。)
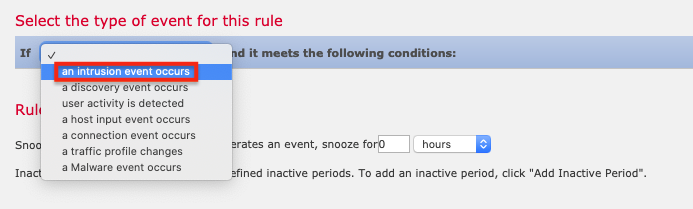
12. 对于条件,选择源国家 > 是 > 朝鲜(例如),然后单击保存。
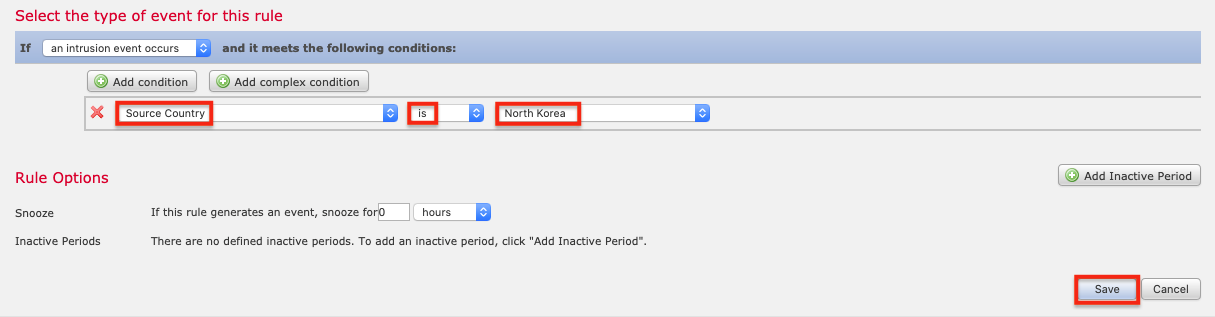
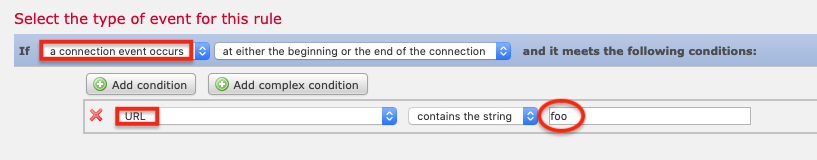
笔记: FMC 可以针对各种不同事件触发补救措施,而不仅仅是入侵。 事实上,在配置补救措施时,您可能希望使用不同的事件类型,以便更容易地触发事件并验证它是否已成功补救。 例如,选择发生连接事件,然后将条件设置为URL > 包含字符串 > foo 。 然后,如果您尝试访问 foo.com,补救规则就会触发。
13. 返回“策略管理”选项卡并单击之前创建的策略(此示例中为“补救”)。 单击“添加规则” 。
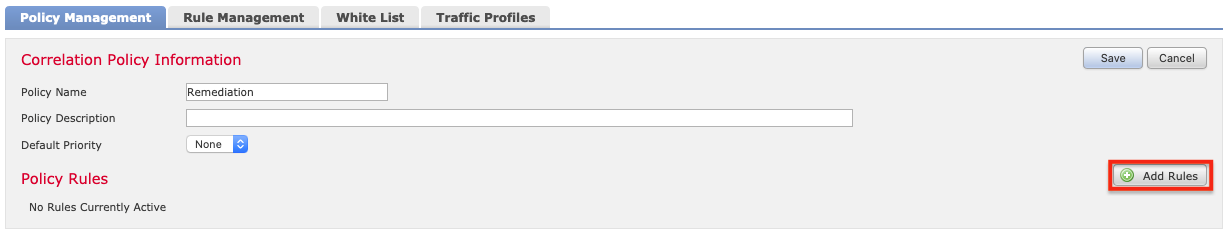
14. 选择 RemediateRule 并单击添加。
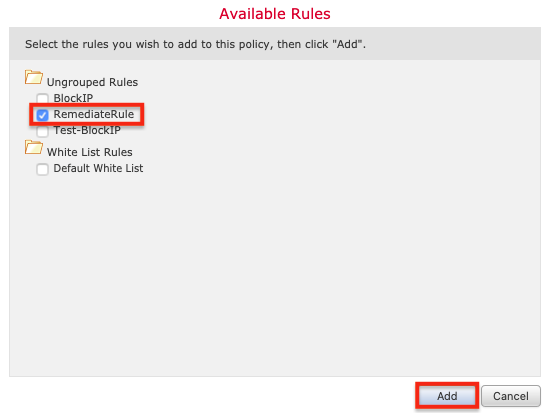
15. 单击“保存” 。
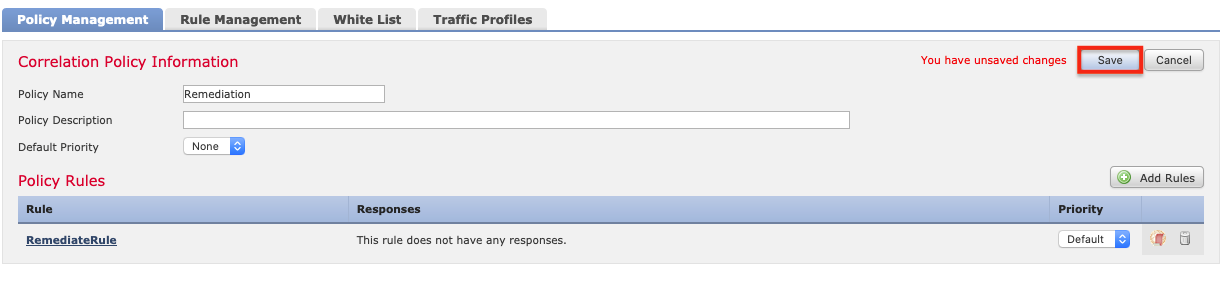
可以使用右侧的切换按钮启用或禁用关联策略。 确保启用了正确的策略。
您可以通过点击“分析”>“关联”>“状态”在 FMC 中查看补救事件的状态。 请参阅结果消息列中的“修复成功完成”消息。
这些推荐做法将 F5 BIG-IP SSL Orchestrator 与 Cisco FTD 一起配置在一个架构中,该架构经过验证,可以解决 SSL 可见性和控制用户场景以及基于 IPS 策略的流量控制和阻止用户场景。 通过 SSL Orchestrator 上的 SSL 终止,FTD 传感器可以提供对入口和出口流量的可见性,以适应和保护组织的应用、服务器和其他资源。 使用基于安全策略的流量控制,组织可以利用此配置并继续扩展,添加更多 FTD 管理的设备,为受保护的网络和应用提供更大的流量容量。 SSL Orchestrator 提供的基于策略的灵活性还可以用来根据业务、安全或合规性要求有选择地将流量引导至不同的资源池。