Apps are the strategy upon which business has staked its digital survival, and F5 Labs research shows they will remain under siege in 2018. This year, let’s resolve to be vigilant in their protection, no matter whether they lie over hill in the data center or over dale in the public cloud.
The New Year is here and, as is the custom, many of us have made resolutions for 2018. Most are usually centered on improvement of some kind. From staying fit to losing weight to spending less and saving more, we resolve to improve ourselves every year.
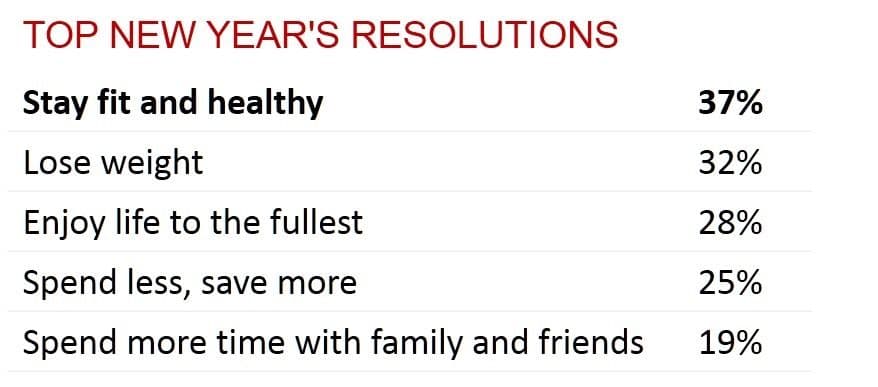
I think perhaps it’s time to also have a New Year’s IT Resolutions. On the top of that list I hope you’ve jotted down the resolution to pay more attention to application protection.
I say that because apps are under siege. Whether it comes from bots lobbing DDoS attacks or malware attempting to mine the security walls erected around apps, the truth is that someone is trying an attack every 39 seconds. That means by the time you read that statistic, a system was attacked.
Maybe one of yours.
When they do attack, they increasingly seek out the most likely vector to succeed: apps and identities. We know that’s the case because our threat research arm, F5 Labs, performed extensive analysis on 443 breaches spanning the last decade. Their research revealed that in 86% of those cases, the attackers went after apps and/or used stolen credentials.
More alarming, perhaps, is both the increase in cases over the past few years as well as the bountiful spoils looted from victims.
In the past decade, attackers have managed to pilfer twelve BILLION records. Yes, you read that right. That’s BILLION. Which is interestingly close to bullion as data records are the digital equivalent of the valuable treasure sought by pirates of old.
And like those pirates of old, today’s attackers use a variety of mechanisms to sneak inside. The sheer volume of stolen credentials has led to an epidemic of credential stuffing attacks. The well-known remediation gap between disclosure of a platform or framework-level vulnerability and patching leads to mass exploitation and success.

Attacks are growing more sophisticated –and automated. We are unlikely to see fewer breaches in 2018. The trend is that we’ll see more. Like sharks circling a disabled ship, attackers are constantly waiting in the wings for an opportunity.
Our expansion into the relatively new, unchartered waters that is multi-cloud only makes security more important. Public cloud brings with it the same risks to apps and data as on-premises, and we must endeavor to focus on protecting them with the same vim and vigor as we do on-premises. That means application services like web application firewalls, identity federation, and app access control. It means employing multi-factor authentication (MFA) when possible, and enforcing security gates no matter where applications are being deployed.
This New Year, let’s resolve to focus on protecting apps. Whether it’s auditing and ramping up existing security programs or initiating new ones, let’s all be more vigilant and engaged with respect to application security in 2018.
You can get a full copy of F5 Labs’ report, “Lessons Learned from a Decade of Breaches”, right here.
About the Author

Related Blog Posts

Why sub-optimal application delivery architecture costs more than you think
Discover the hidden performance, security, and operational costs of sub‑optimal application delivery—and how modern architectures address them.

Keyfactor + F5: Integrating digital trust in the F5 platform
By integrating digital trust solutions into F5 ADSP, Keyfactor and F5 redefine how organizations protect and deliver digital services at enterprise scale.

Architecting for AI: Secure, scalable, multicloud
Operationalize AI-era multicloud with F5 and Equinix. Explore scalable solutions for secure data flows, uniform policies, and governance across dynamic cloud environments.

Nutanix and F5 expand successful partnership to Kubernetes
Nutanix and F5 have a shared vision of simplifying IT management. The two are joining forces for a Kubernetes service that is backed by F5 NGINX Plus.

AppViewX + F5: Automating and orchestrating app delivery
As an F5 ADSP Select partner, AppViewX works with F5 to deliver a centralized orchestration solution to manage app services across distributed environments.
F5 NGINX Gateway Fabric is a certified solution for Red Hat OpenShift
F5 collaborates with Red Hat to deliver a solution that combines the high-performance app delivery of F5 NGINX with Red Hat OpenShift’s enterprise Kubernetes capabilities.
