In his recent article in Forbes, Richard Stiennon’s claim that There Is No Cloud Security Market Segment stirred some interesting discussions about the need to change the way we view cloud security. Indeed, cloud continues to be a driver for change. Asignificant majority (87%) of organizations operate applications in a multi-cloud model that includes an average of 2-6 different providers. This reality is forcing organizations to consider changes to everything from tools to team structures.
Along with expansion to the cloud, there is a shift in architectures and how applications are being built.
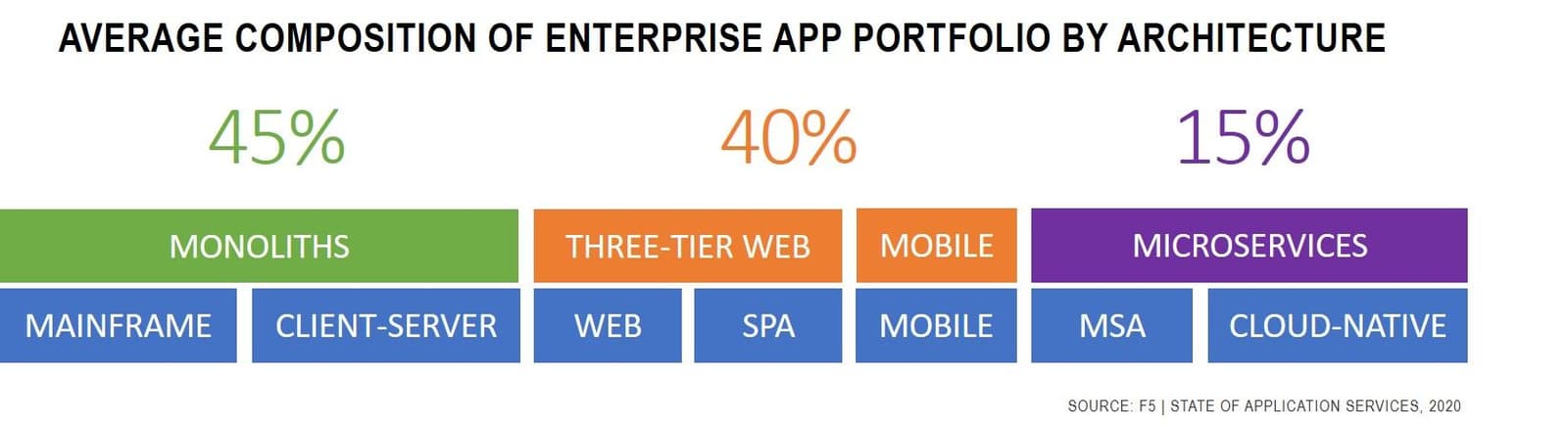
Our research indicates that every organization is in a state of change today. Whether driven by a desire to lead in a digital economy or accelerated by COVID, organizations are rapidly embarking on an application modernization journey as part of their digital transformation efforts. This change is evident in the composition of the enterprise app portfolio. Today, 15% already leverage modern application architectures. This is significant growth, given that microservices only gained traction as an architecture around 2014 and Kubernetes, the dominant mechanism by which such applications are delivered, deployed, and operated, was officially released in 2015. With less than five years to mature, these modern architectures are already consuming a significant amount of enterprise mindshare.
But, as the French writer Jean-Baptiste Alphonse Karr said in 1848, “plus ça change, plus c'est la même chose." English speakers will recognize this as the more familiar, "the more things change, the more they stay the same."
In the domain of security—and specifically the problems experienced by customers—this is particularly poignant and true yet today.
Here's where the old axiom about change enters the stage: Despite changes in architectures and location, security problems do not change. Customers still need to protect applications, ensure availability, and defend against DDoS attacks. Application security is a bigger challenge due to the expanding attack surfaces and vulnerabilities.
New architectures and locations, same security challenges.
Richard put it very aptly in his Forbes’ article, classifying customer security challenges this way:
"In other words a ‘cloud security’ vendor is really a general purpose security provider for modern computing infrastructures. They may enforce policies across micro-segments (network security) or harden the VMs or containers against attack (endpoint security) or encrypt data in motion or at rest (data security). They may enforce access to cloud applications based on identity (IAM). In other words, all of the cloud security providers can be put into network, endpoint, data, or IAM categories."
While challenges may be the same, the operational approaches and technology customers need to solve these security problems must change. The spread of applications and their users along with the scale of attacks necessitates a new approach to solving the same old security problems. One of the core tenets of this new paradigm is to shift from point security solutions with dependency for inline inspection to a broader holistic approach to security. In that sense, a general security provider cannot address or extend their capabilities to address the security challenges in the new world. For starters, the convenient choke points used by general security providers at well-defined perimeters are non-existent in the new world. Another model of delivery as a service (a.k.a. SASE) is possible for only a subset of security challenges, most of which can be addressed by the cloud/compute providers themselves!
At F5, we're committed to delivering a new approach and offering customers a better way to solve their security challenges, no matter the architecture or location of their applications. We believe that a new approach to security that aligns with the faster operational pace of modern application development is necessary. We've embarked on a path to a multi-purpose application analytics platform that, by its very nature, provides the foundation needed to develop services using new techniques that scale to meet the challenge of today's attacks.
About the Author
Related Blog Posts

Multicloud chaos ends at the Equinix Edge with F5 Distributed Cloud CE
Simplify multicloud security with Equinix and F5 Distributed Cloud CE. Centralize your perimeter, reduce costs, and enhance performance with edge-driven WAAP.
At the Intersection of Operational Data and Generative AI
Help your organization understand the impact of generative AI (GenAI) on its operational data practices, and learn how to better align GenAI technology adoption timelines with existing budgets, practices, and cultures.
Using AI for IT Automation Security
Learn how artificial intelligence and machine learning aid in mitigating cybersecurity threats to your IT automation processes.
Most Exciting Tech Trend in 2022: IT/OT Convergence
The line between operation and digital systems continues to blur as homes and businesses increase their reliance on connected devices, accelerating the convergence of IT and OT. While this trend of integration brings excitement, it also presents its own challenges and concerns to be considered.
Adaptive Applications are Data-Driven
There's a big difference between knowing something's wrong and knowing what to do about it. Only after monitoring the right elements can we discern the health of a user experience, deriving from the analysis of those measurements the relationships and patterns that can be inferred. Ultimately, the automation that will give rise to truly adaptive applications is based on measurements and our understanding of them.
Inserting App Services into Shifting App Architectures
Application architectures have evolved several times since the early days of computing, and it is no longer optimal to rely solely on a single, known data path to insert application services. Furthermore, because many of the emerging data paths are not as suitable for a proxy-based platform, we must look to the other potential points of insertion possible to scale and secure modern applications.