The global digital economy requires application programming interfaces (APIs) to connect application-based services to customers, consumers, partners, and employees. Legacy, modernized, and new applications are evolving towards API-based architectures to accelerate application development and reduce time-to-market. Moving application functionality closer to the customer to reduce friction is the genesis of decentralized architectures and the API-first movement.
Unfortunately, the efficiencies gained through APIs in application development are becoming overshadowed by the risk they introduce to an IT enterprise. Hackers have learned that compromising APIs is easy when they are lightly protected or not protected. No one would argue that APIs require secure practices; however, there is no industry consensus on the best way to secure them. The following are some of the top reasons APIs require more protection than they usually may receive.
API Vulnerabilities are Largely Unaddressed
A growing number of significant security breaches owing to poor API visibility and security occur and will continue for the foreseeable future.1 The race toward digitizing organizations will put more inadequately protected APIs into production. Many organizations will attempt to solve API vulnerabilities through better design and coding, only to realize the same security failings as applications in general—partly because security is not a core competency for a typical application developer, and security teams may not be aware of all the third-party interconnections within their environment.
API Sprawl is Shockingly Pervasive
The core of API sprawl is the lack of a holistic strategy that includes governance and best practices. Agile application development has led to multiple versions of the same API without the benefit of API version control. The move to microservices results in an application comprising many dozens of APIs.
Unmanaged APIs create rogue, shadow, and zombie APIs. APIs will approach 2 billion by 2030, further exacerbating the problem.2
API Gateways are Insufficient to Secure APIs in Complex Ecosystems
Operating in a distributed cloud environment is the norm today. However, using a dedicated API gateway as a single-entry point to control security has limitations, including single points of failure and performance degradation. Since API gateways today are a critical component of API infrastructure, it became evident that the proliferation of APIs increases the deployment of API gateways—leading to API gateway sprawl.
Web Application Firewalls (WAFs) Only Partially Protect APIs
Modern WAFs provide robust protection and security for API protocols, including GraphQL and gRPC, and provide a stopgap for critical software vulnerabilities—but often they do not offer the necessary observability of APIs to detect advanced threats across hybrid and multi-cloud architectures. Many WAFs lack dynamic API discovery, automated detection and threat mitigation, testing, and OpenAPI document specification automation and enforcement capabilities.
Now that we know why hackers love APIs, how can we protect them?
Leverage Regulations and Standards to Garner Support for API Protection Projects
Regulators have taken notice of the risk introduced by APIs and encouraged companies to mitigate their risk throughout their IT enterprises, including third parties. The U.S. Department of the Treasury and the Consumer Financial Protection Bureau (CFPB) issued strong guidance to complying entities needing to protect APIs. From a standards perspective, PCI DSS v4 requirement 6.3.2 requires API security, and NIST 800-95 Guide to Secure Web Services recommendation since 2007 – 800-24 Security Strategies for Microservices-based Application Systems specifies secure API management.
Focus on the Architecture
An API security architecture must consider integrating with a distributed IT enterprise, including multi-cloud, regional edges, and service tiers. The solution should be deployable to any hardware, virtualized environment, docker, Kubernetes, etc. The solution must allow security policies to follow the API through its ecosystem. The following is an example of a reference architecture for securing APIs.
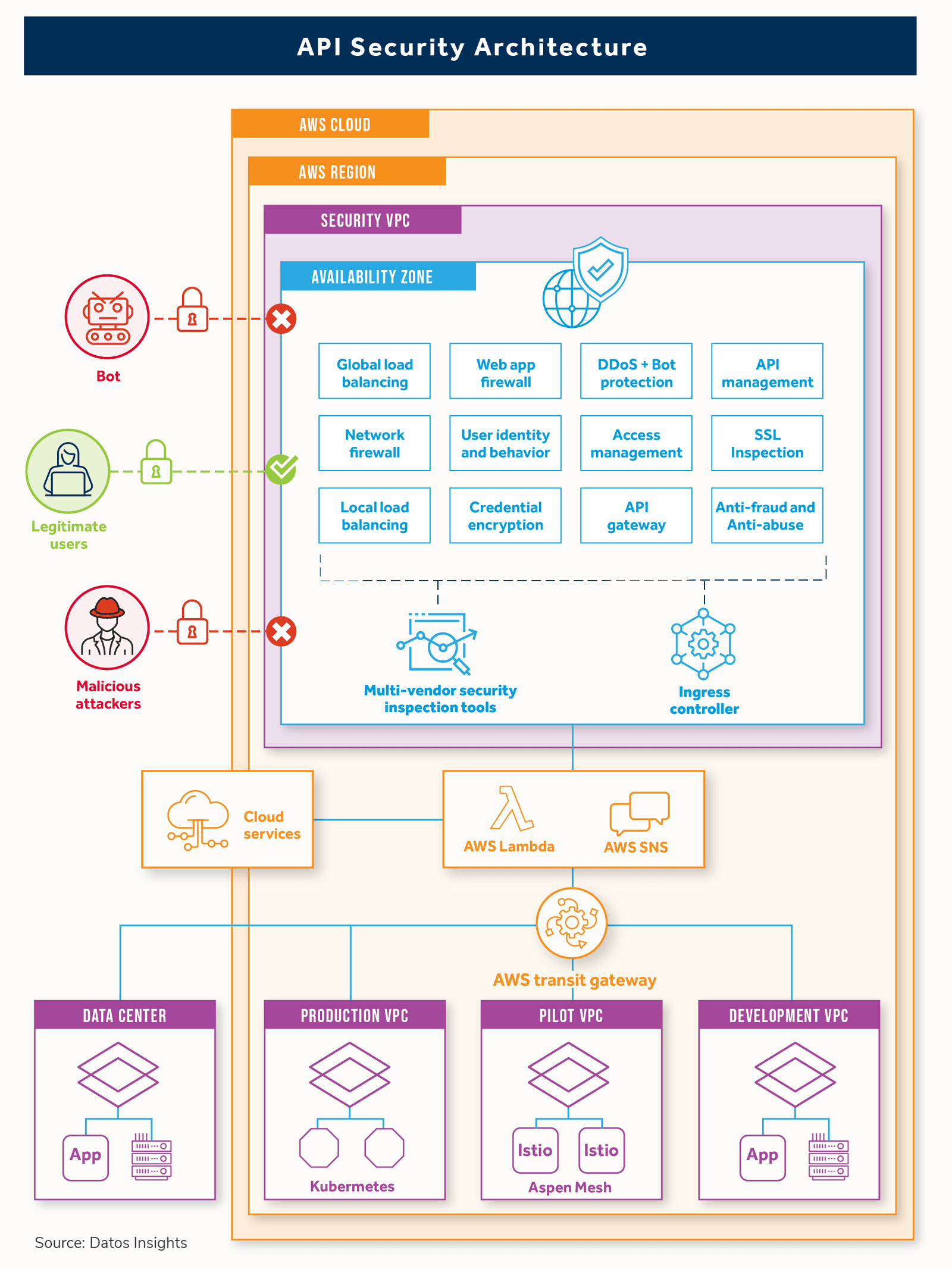
Final Thoughts
Hackers have long realized that APIs suffer the same security maladies as web applications, including weak authentication and authorization controls. They have become adept at exploiting API vulnerabilities, abusing business logic, and creating zero-day exploits to access IT enterprises with little resistance.
Personal data is the property of the individual, not an application or service provider. The digital economy fuels open data sharing. APIs enable private, public, partner, and third-party data and services. APIs need to have privacy-preserving technologies applied to comply with data privacy regulations.
Deploying an API security solution requires infrastructure integration and connectors, some custom to deploy in an IT estate properly. Understanding the intricacies of deployment requires architectural planning. Selecting a solution that operates out of the box within an existing IT enterprise architecture reduces deployment time.
To learn more about defending against API attacks, check out my recent report commissioned by F5, API Security Solution Evaluation Guide. This report discusses the most important considerations of selecting an API protection solution.
By Tari Schreider, C|CISO, CRISC – Strategic Advisor, Datos Insights
Footnotes:
1 Ian Dinno, Lesson Learned (So Far) from the T-Mobile breach, F5, February 8, 2023
2 Rajesh Narayanan, Mike Wiley, Continuous API Sprawl, F5, November 4, 2021
3 Rajesh Narayanan, Distributed Gateway Actors: Evolving API Management, F5, June 23, 2023
About the Author
Related Blog Posts

Why sub-optimal application delivery architecture costs more than you think
Discover the hidden performance, security, and operational costs of sub‑optimal application delivery—and how modern architectures address them.

Keyfactor + F5: Integrating digital trust in the F5 platform
By integrating digital trust solutions into F5 ADSP, Keyfactor and F5 redefine how organizations protect and deliver digital services at enterprise scale.

Architecting for AI: Secure, scalable, multicloud
Operationalize AI-era multicloud with F5 and Equinix. Explore scalable solutions for secure data flows, uniform policies, and governance across dynamic cloud environments.

Nutanix and F5 expand successful partnership to Kubernetes
Nutanix and F5 have a shared vision of simplifying IT management. The two are joining forces for a Kubernetes service that is backed by F5 NGINX Plus.

AppViewX + F5: Automating and orchestrating app delivery
As an F5 ADSP Select partner, AppViewX works with F5 to deliver a centralized orchestration solution to manage app services across distributed environments.
F5 NGINX Gateway Fabric is a certified solution for Red Hat OpenShift
F5 collaborates with Red Hat to deliver a solution that combines the high-performance app delivery of F5 NGINX with Red Hat OpenShift’s enterprise Kubernetes capabilities.