Threat Stack is now F5 Distributed Cloud App Infrastructure Protection (AIP). Start using Distributed Cloud AIP with your team today.
Author’s note: This blog post is the first in a two-part series around how Threat Stack approaches its UI design for cybersecurity use cases. The implemented changes are based on honest customer feedback as we continue on our path of innovation.
At Threat Stack, we take our customer feedback very seriously and love a good challenge! While our UI continues to embrace modernity, we sought to identify new patterns and assets that could be proactively implemented to make our user experience even better. Over the past year, we’ve made some iterative changes to our user interface (UI). We updated crucial components, color schemes, introduced dark mode, and added features to improve usability to allow our users to detect and respond to incidents quickly with an interface that works best for them.
Recently we announced updates to our platform that enable organizations to accelerate audits and meet compliance requirements. These enhancements are a direct result of one of Threat Stack’s core missions, to make compliance easily achievable and to make our rich telemetry seamless to navigate. Mean-time-to-know (MTTK) is an important metric used to measure ease of use, and when our users are investigating an incident, every click and keystroke counts and is critical for a quick response.
Based on this knowledge and feedback from several customers and key stakeholders, we identified that the rules page was an excellent contender for further reducing MTTK. In addition, it would allow us to embrace new concepts like guided navigation, machine learning, and data visualization.
Out With the Old and In With The New
After interviewing customers to discuss proposed changes, it was evident that while the legacy rules page was fulfilling its intended purpose, it was time to innovate again! Looking ahead to new functionality, such as our recommendation engine driven by powerful machine learning (ML) technology, rule labels, and data visualizations, we quickly realized there was a need to explore a revamped user experience. This would allow customers to effectively take advantage of these advanced features and traverse Threat Stack’s industry-leading rules.
The previous rules page was undoubtedly ahead of its time and served its purpose well but was limited to providing a hierarchical view of the environment, making it an involved process to leverage this new enriched context effectively.

This screenshot shows how to apply our PCI ruleset to servers in the legacy Threat Stack UI.
The Power of Customer Feedback
After sharing our upcoming new features and technology with a number of customers, we determined the following core needs:
- A faceted search system allowing customers to navigate existing rules data and accommodate new telemetry such as rule labels and our rules recommendation engine
- The ability to bulk manage rules to more efficiently toggle active rules and rulesets within the organization
- The ability to view rules and rule context across multiple rules sets to quickly discern duplicate or dated custom rules
- An efficient way to provide proof of compliance to auditors
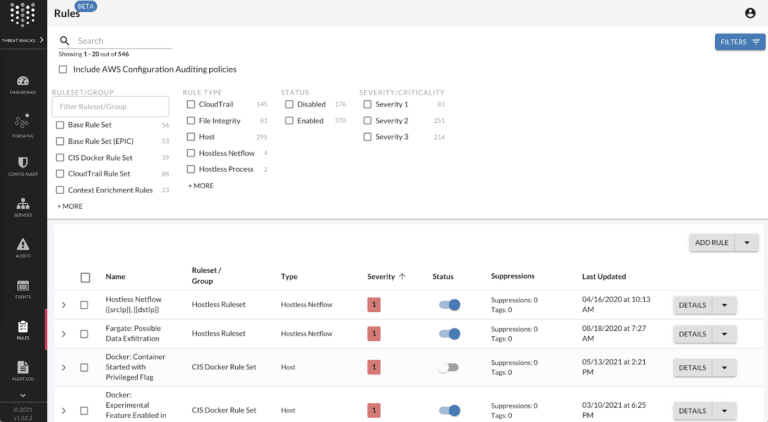
This screenshot shows Threat Stack’s new top-level Rules page design.
Our solution to these core needs was to investigate Elastic App Search. This open source tool provides aggregation and powerful search functionality, allowing our customers to locate rules in need of updating. Through Elastic App Search, we can now give the users predefined filters such as rule type, status, and severity to hone in on rules of interest. Additionally, by providing search functionality, users can further drill into their organization’s rules through text-based querying on the rule name.
Furthermore, over the past year, we also worked to move our components to Material UI to generate modern reusable components such as tables, pagination, and action buttons. The rules page was an excellent contender to prioritize for this effort, providing a more consistent UI experience for our users. Additionally, to address rules management, we moved our hierarchical rules organization into a table, which provides the ability to sort by column, select multiple rules (regardless of ruleset), and bulk-edit rule status across numerous rule sets.
We also became aware that as we were adding new context to our rules, we needed to visualize the context in the individual rules view more easily. Therefore, we reorganized the rules details page to feature prominent information first. The newly added rules histogram allows users to identify if the selected rule is suitable for tuning quickly. Lastly, we implemented the function of a read-only rule that can easily be shared with auditors who are looking for proof of compliance. As the Threat Stack Cloud Security Platform® continues to evolve and innovate, so will its UI. Please stay tuned for part two of this blog series to hear more about how further enrichments to the platform will impact the UI experience for our customers.
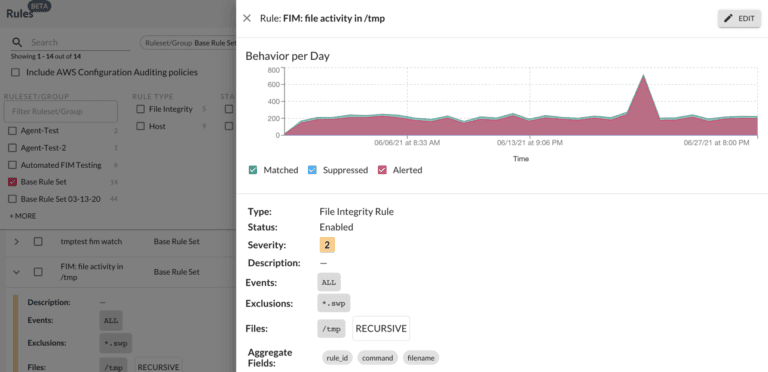
This screenshot shows Threat Stack’s redesigned Rule details view, prominently displaying our newly added rules histogram that allows users to quickly identify if the selected rule is a candidate for tuning.
Threat Stack Rules Continue to Pioneer Innovation
Guided navigation is a concept that we have been exploring at Threat Stack for a number of our UI features. The rules page became the top contender for piloting guided navigation within cybersecurity use cases.
As a result, customers could reduce duplicate rules, quickly modify rule context, and identify rules that needed to be adjusted to maintain compliance. The new rules page has proven to be a great way to reduce MTTK. There is a trickle-down effect on reduced false positives and less maintenance of overall cybersecurity posture by providing improved rules management.
Future Consideration
In the future, we will be looking to leverage the new rules page as it grows to include rules metadata. In addition, the alerts and servers pages will receive similar treatment, and we look forward to working with our customers to continue refining what the future of the Threat Stack UI is going to look like.
Threat Stack is now F5 Distributed Cloud App Infrastructure Protection (AIP). Start using Distributed Cloud AIP with your team today.
About the Author
Related Blog Posts
SaaS-first strategies reshape cloud-native application delivery
F5 NGINXaaS empowers cloud and platform architects to unify operations, reduce complexity, and deliver exceptional digital experiences at scale.

F5 ADSP Partner Program streamlines adoption of F5 platform
The new F5 ADSP Partner Program creates a dynamic ecosystem that drives growth and success for our partners and customers.

Accelerate Kubernetes and AI workloads with F5 BIG-IP and AWS EKS
The F5 BIG-IP Next for Kubernetes software will soon be available in AWS Marketplace to accelerate managed Kubernetes performance on AWS EKS.
F5 NGINX Gateway Fabric is a certified solution for Red Hat OpenShift
F5 collaborates with Red Hat to deliver a solution that combines the high-performance app delivery of F5 NGINX with Red Hat OpenShift’s enterprise Kubernetes capabilities.
F5 Silverline Mitigates Record-Breaking DDoS Attacks
Malicious attacks are increasing in scale and complexity, threatening to overwhelm and breach the internal resources of businesses globally. Often, these attacks combine high-volume traffic with stealthy, low-and-slow, application-targeted attack techniques, powered by either automated botnets or human-driven tools.
Phishing Attacks Soar 220% During COVID-19 Peak as Cybercriminal Opportunism Intensifies
David Warburton, author of the F5 Labs 2020 Phishing and Fraud Report, describes how fraudsters are adapting to the pandemic and maps out the trends ahead in this video, with summary comments.