The micro-movement is beginning to take over the data center, from the inside out. As developers begin to embrace microservices for applications, network architects are looking at microsegmentation in the network.

There’s a movement afoot in development, specifically in the architectural realm. That movement is towards microservices and away from the monolithic applications of the past.
Supported by emerging technology like containerization and cloud, microservices seek to improve stability, agility and scale by decomposing applications into smaller, locally focused services.
Simultaneously, network architects are moving in the same direction, decomposing monolithic network architectures into microsegmented domains with heightened application awareness. Their goal? To enable stability, agility and scale of network services critical for success in an application economy.
Together, these micro-movements are changing the face of the data center; bifurcating into a two-tiered architecture designed for agility, speed and reliability.
MICROSERVICES
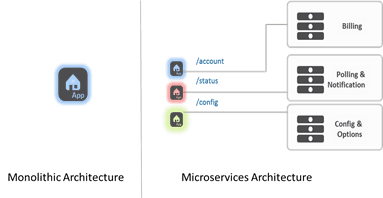
What was once a monolithic web application comprising thousands of lines of code becomes a set of decoupled microservices, each consisting of only hundreds of lines of code and laser-focused on a particular functional capability.
Microservices may seem at first to be just another variation on the theme of SOA (Service Oriented Architecture) which also claimed to break down monolithic apps into more focused services. While that core principle remains true, microservices avoid the complex superstructure associated with SOA to enable the rapid, agile evolution of services without concern for longevity or dependencies.
The implication for development quality and pipeline is notable as fewer lines of code are easier to troubleshoot, maintain and modify in rapid fashion.
It also has an impact on the network architecture and services required to deliver microservices. A monolithic, single-tiered network architecture is unlikely to provide the operational velocity and scale required to support the delivery of hundreds – or thousands – of microservices.
MICROSEGMENTATION
On the other side of the IT wall, network architects are simultaneously rethinking the premises upon which they have designed the network. Cloud and mobility have pushed network scalability to its limits and microservices are likely to be the straw that breaks that camel’s back. A new approach is necessary, and that approach is often referred to as microsegmentation.
Like microservices, microsegmentation is a decomposition-based approach to architecture that breaks up network services into local and more manageable components. Initially proposed as a better security model, microsegmentation is wholly appropriate for other application affine services such as load balancing, caching, acceleration and application security.
By both physically and logically moving these services closer to the applications (or services) they are responsible for delivering, network architecture becomes more agile and resilient to change, as change is constrained locally to the application or service in question.
TWO-TIERED DATA CENTER ARCHITECTURE
The resulting mix of microservices and microsegmentation are effectively a split in the data center architecture. Core, shared services remain at the traditional edge of the network, while per-application services migrate, pulled inward towards the application center of gravity. Core, shared services like corporate access via SSL VPN, corporate network and application protection against DDoS attacks and similar services will serve as the backbone of this new two-tiered architecture. Per-application services such as caching, load balancing and application security will populate the second-tier of the data center architecture.

Per-application (or per-service) infrastructure enables greater logical coupling of services with the applications they deliver, and when deployed in a software or virtual form factor enable greater agility and control across the entire lifecycle of the application or service. That’s increasingly important in an environment where microservices may have a lifespan of only a few months, as per-application services must be set up and torn down with equal alacrity.
These per-application services will be deployed using a microsegmentation approach; with granular policies governing smaller, focused scalability and security domains based on responsibility for a given microservice or set of related microservices.
The micro-movement is only in its infancy, but it is gaining rapid speed as organizations born in the cloud and those with large, complex and often unwieldy network architectures look for new ways to simplify and scale the services necessary for success.
Microservices and microsegmentation align both application and network architecture in a way that enables both to simultaneously scale and speed the delivery of the applications critical to success in an application world.
About the Author

Related Blog Posts

Why sub-optimal application delivery architecture costs more than you think
Discover the hidden performance, security, and operational costs of sub‑optimal application delivery—and how modern architectures address them.

Keyfactor + F5: Integrating digital trust in the F5 platform
By integrating digital trust solutions into F5 ADSP, Keyfactor and F5 redefine how organizations protect and deliver digital services at enterprise scale.

Architecting for AI: Secure, scalable, multicloud
Operationalize AI-era multicloud with F5 and Equinix. Explore scalable solutions for secure data flows, uniform policies, and governance across dynamic cloud environments.

Nutanix and F5 expand successful partnership to Kubernetes
Nutanix and F5 have a shared vision of simplifying IT management. The two are joining forces for a Kubernetes service that is backed by F5 NGINX Plus.

AppViewX + F5: Automating and orchestrating app delivery
As an F5 ADSP Select partner, AppViewX works with F5 to deliver a centralized orchestration solution to manage app services across distributed environments.
F5 NGINX Gateway Fabric is a certified solution for Red Hat OpenShift
F5 collaborates with Red Hat to deliver a solution that combines the high-performance app delivery of F5 NGINX with Red Hat OpenShift’s enterprise Kubernetes capabilities.
