Application security is a fundamental component of F5’s ADC platform, with the BIG-IP delivering industry-leading web application firewall protection, as well as secure, unified access for applications located anywhere within a multi-cloud architecture. And while we may stake a claim for providing the most comprehensive security solution available, we won’t pretend to be the only player in the market, thus complicating a buyer’s decision due to the myriad of alternatives being considered. However, for those looking to mitigate attacks on applications deployed in the public cloud, AWS has taken a step to simplify the consideration phase of the buyer's journey with the release of their AWS Security Competency program, within which F5 recently announced the inclusion of its web application firewall, BIG-IP Application Security Manager (ASM). In this post, we’re going to dive deeper into how F5’s WAF solution—delivering advanced L7 application and DDoS protection—became a member of this exclusive club…
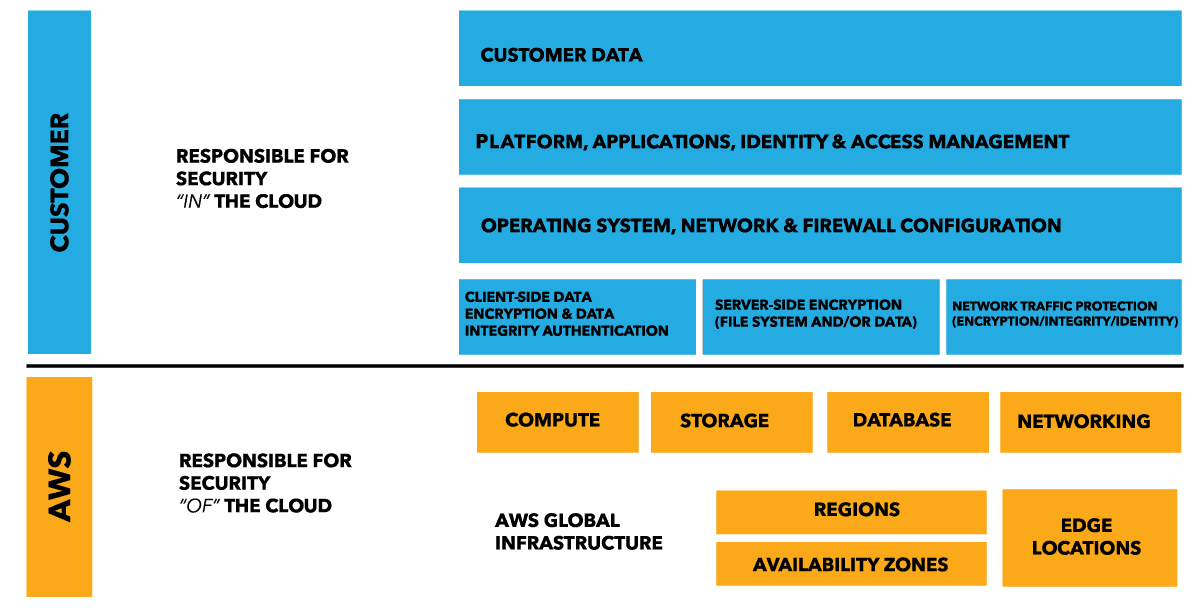
AWS continues to stress the importance of its shared responsibility model (Figure 1, above), whereby application owners are accountable for the security inthe cloud (virtual machines, OS, applications, and data), while AWS is responsible for the security of the cloud (hardware, software, networking & facilities). This is where the Security Competency program comes into play, by presenting AWS users with a concise list of third-party vendors who have demonstrated success and technical proficiency in delivering security solutions for AWS-hosted applications in the cloud, essentially eliminating a number of inadequate vendors from the consideration list.
The 3 Categories of Requirements to Achieve AWS Security Competency
Gaining AWS Security Competency was no stroll in the park, with partners needing to comply with a multitude of requirements across three distinct areas:
The first of these centers around customer references and essentially proving the solution's value. To check this box, F5 supplied AWS with a number of completed security project reports, intricately describing customer problem statements and how F5’s WAF provided the solution. Of these customer stories, two were publicly endorsed to further illustrate a selection of use cases and benefits in production environments.
The second category focused on product and deployment functionality, as well as any general functionality specific to the AWS infrastructure. To pass here, F5 was required to present thorough documentation on the configuration, usage, and proficiencies of the BIG-IP ASM Virtual Edition, as well as dedicated guidelines on deploying the WAF in a highly available (HA) topology. As part of the documentation, AWS explicitly requires F5 to provide a list of all compliance regulations the solution assists with, making it easier for customers to disregard other vendors who may fall short of expectations. Finally, the WAF solution's ability to encrypt data was verified, before showcasing its deep integration with AWS’ IAM role-based management service, ensuring users are able to securely regulate access to the device.
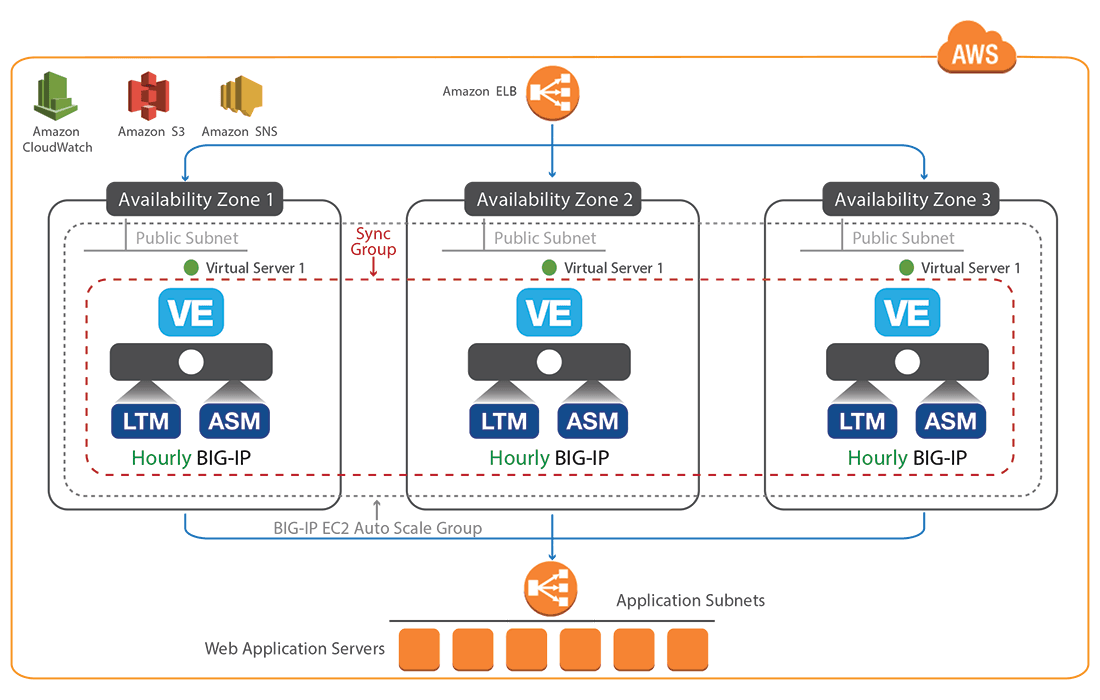
The third and final set of requirements concentrate on the WAF’s integration with AWS services to enhance the security and availability of the solution. As F5’s WAF solution supports auto scaling via a CloudFormation template—as described in this previous post and shown in Figure 2—it passed the ‘infrastructure security’requirements by integrating with AWS Auto Scale and AWS ELB, while also exhibiting the ability to operate across multiple availability zones. Next up, ‘logging and monitoring’ — another easy checkmark here with the auto scaling solution relying heavily on AWS CloudWatch to monitor instances in real-time to provide alarms and trigger scaling events. For the final hurdle, the AWS Security team performed a vulnerability assessment of the WAF, before ensuring it met all data protection requirements and supported the necessary identity and access obligations.

After passing all requirements with flying colors, AWS has subsequently published F5’s WAF solution to its Security Partner Solutions page for all to see, while also providing F5 with this shiny new accolade in recognition of this achievement:
To get the facts on F5’s WAF solution, you can take a look at the BIG-IP ASM datasheet, or alternatively you can check it out on the AWS Marketplace here.
About the Author

Related Blog Posts

Why sub-optimal application delivery architecture costs more than you think
Discover the hidden performance, security, and operational costs of sub‑optimal application delivery—and how modern architectures address them.

Keyfactor + F5: Integrating digital trust in the F5 platform
By integrating digital trust solutions into F5 ADSP, Keyfactor and F5 redefine how organizations protect and deliver digital services at enterprise scale.

Architecting for AI: Secure, scalable, multicloud
Operationalize AI-era multicloud with F5 and Equinix. Explore scalable solutions for secure data flows, uniform policies, and governance across dynamic cloud environments.

Nutanix and F5 expand successful partnership to Kubernetes
Nutanix and F5 have a shared vision of simplifying IT management. The two are joining forces for a Kubernetes service that is backed by F5 NGINX Plus.

AppViewX + F5: Automating and orchestrating app delivery
As an F5 ADSP Select partner, AppViewX works with F5 to deliver a centralized orchestration solution to manage app services across distributed environments.
F5 NGINX Gateway Fabric is a certified solution for Red Hat OpenShift
F5 collaborates with Red Hat to deliver a solution that combines the high-performance app delivery of F5 NGINX with Red Hat OpenShift’s enterprise Kubernetes capabilities.
