F5 Labs recently published our annual Application Protection Report. The 2022 edition is subtitled “In Expectation of Exfiltration,” reflecting the enduring value of stolen data to attackers, whether they use it for fraud or ransom. The report synthesizes data from several disparate sources to understand the evolution of the threat landscape over time, the relationship between organizations’ characteristics and the attack techniques they face, and—most importantly—what security practitioners can do to mitigate the risks.
The (Continued) Rise of Ransomware
Much of the focus of the report is on the continuing growth of ransomware, and with good reason: in 2021 ransomware techniques featured in 42% of application attacks leading to U.S. data breaches. However, the focus on ransomware should not obscure the risk of non-encrypting malware, which also grew dramatically, and tended to result in exfiltration of data without encryption. Overall, malware attacks of any kind featured in more than 30% of all attacks in 2021 that led to U.S. data breaches.
Speaking of data exfiltration, we chose the subtitle for the report when we found that exfiltration became dramatically more common in 2021. Four out of five application attacks that resulted in U.S. data breaches featured exfiltration as a tactic, including Magecart attacks, additional web attack campaigns, ransomware attacks, and other kinds of malware infections. Given the explosive growth of ransomware in 2020, and the appearance in early 2021 that ransom was surpassing fraud as a way to profit from cyberattacks, this finding surprised us, and indicates that fraud will continue to compete with ransom as a monetization strategy.
The Role of Web Exploits
We also found that web exploits appeared to play a diminished role in data breaches, though this isn’t the whole story: while the proportion of web exploit-driven breaches decreased, the web exploits that were reported were nearly all of the type known as formjacking attacks, of which Magecart is the best-known example. Even as web exploits appear to become less common, they are becoming more focused on comparatively easy and low-touch attack chains that reap payment card numbers at large scale. This trend reflects the enduring value that payment card numbers have compared with other kinds of less-fungible data, especially considering that retail and other e-commerce targets of formjacking also tended to be the least frequent victims of ransomware.
Furthermore, while sophisticated campaigns by state-sponsored actors tend not to show up in our sources, a few known advanced attacks in our data set made clever use of web exploits to perpetrate precision attacks against organizations, reflecting that the largest numbers don’t always capture the risk that matters the most. While web exploits aren’t the go-to tactic the way they were a few years ago, vulnerability management and exploit protection are still enormously important for defense.
What Organizations Are Doing Today
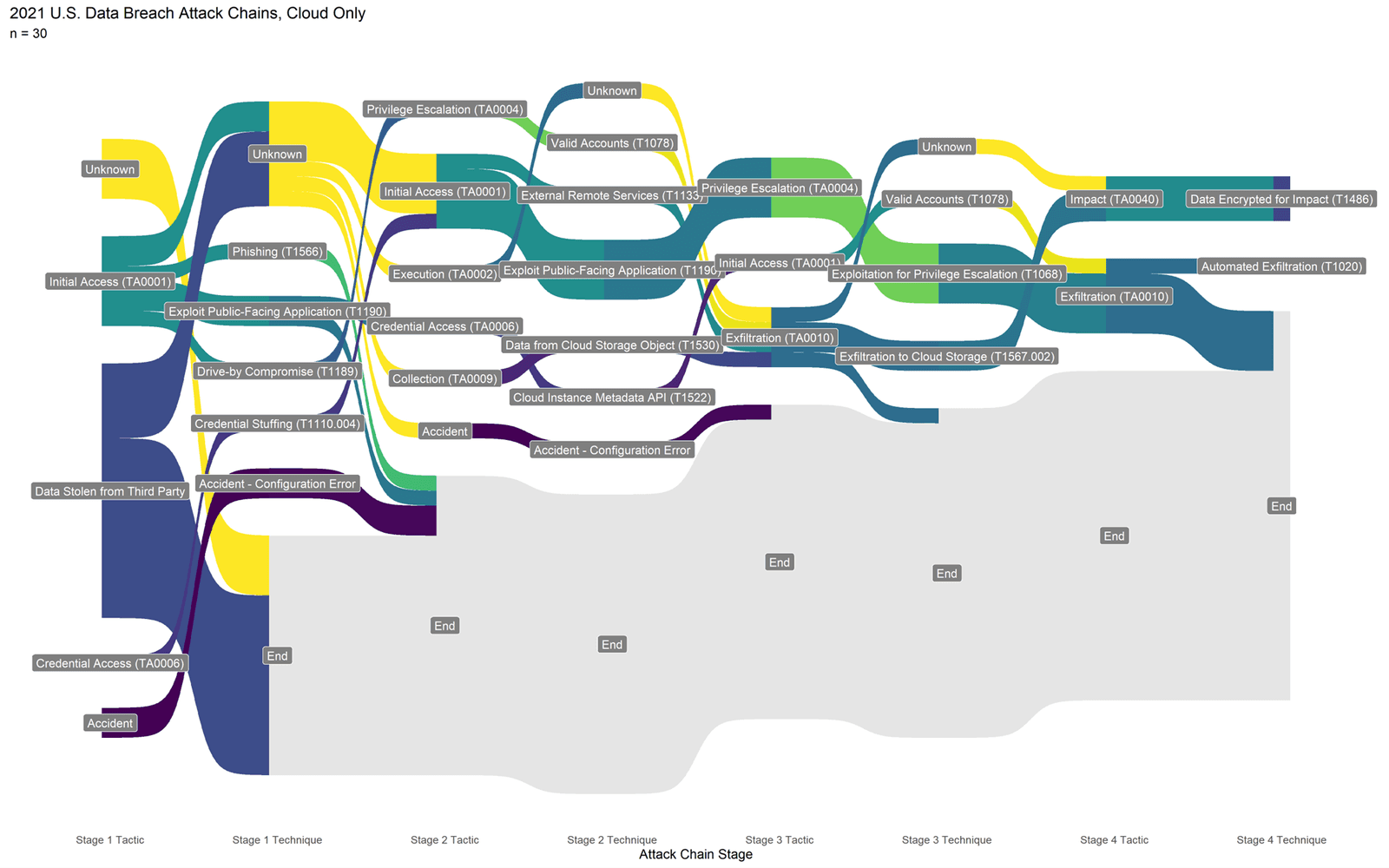
The report also examines the state of cloud security, finding that third- and fourth-party relationships in the cloud tended to make risk manifest in unexpected ways, and that access control misconfigurations were significantly more likely to produce a data exposure than malicious activity.
The recommended mitigations in the report are sorted in various ways depending on the operational priorities of different organizations, but control objectives such as data backup, network segmentation, and various forms of environmental hardening tended to rise to the top of the list no matter how it was sorted. The report also features the same attack chain analysis and visualization approach using the MITRE ATT&CK® framework that the team debuted in the 2021 report.
F5 Labs to Present Research at RSAC in June
We are excited to share that a certain lead researcher on the Application Protection Report will be presenting this research at the RSA Conference in San Francisco. In addition to exploring these trends in greater detail, we'll be covering a wide range of less prominent but no less interesting attack behaviors. There's no shortage of amazing work at RSA, but if trends in attacker targeting are useful to you, consider stopping by Moscone South 208 at 1:15 p.m. Pacific on Wednesday, June 8. More information available here. And if you can’t make it to San Francisco but would like more detail, or to take a deeper dive into the data, just head over to F5 Labs.
About the Author
Related Blog Posts

AppViewX + F5: Automating and orchestrating app delivery
As an F5 ADSP Select partner, AppViewX works with F5 to deliver a centralized orchestration solution to manage app services across distributed environments.

Build a quantum-safe backbone for AI with F5 and NetApp
By deploying F5 and NetApp solutions, enterprises can meet the demands of AI workloads, while preparing for a quantum future.

F5 ADSP Partner Program streamlines adoption of F5 platform
The new F5 ADSP Partner Program creates a dynamic ecosystem that drives growth and success for our partners and customers.
F5 NGINX Gateway Fabric is a certified solution for Red Hat OpenShift
F5 collaborates with Red Hat to deliver a solution that combines the high-performance app delivery of F5 NGINX with Red Hat OpenShift’s enterprise Kubernetes capabilities.
F5 Silverline Mitigates Record-Breaking DDoS Attacks
Malicious attacks are increasing in scale and complexity, threatening to overwhelm and breach the internal resources of businesses globally. Often, these attacks combine high-volume traffic with stealthy, low-and-slow, application-targeted attack techniques, powered by either automated botnets or human-driven tools.
Phishing Attacks Soar 220% During COVID-19 Peak as Cybercriminal Opportunism Intensifies
David Warburton, author of the F5 Labs 2020 Phishing and Fraud Report, describes how fraudsters are adapting to the pandemic and maps out the trends ahead in this video, with summary comments.