- Ansible 2.5 is now available
- New F5 modules have been added with more security profiles, licensing support, and monitoring
- You can get more information about our portfolio of F5 Ansible modules on Github
Automation is a core component of the DevOps approach to deployments currently sweeping through enterprise IT. While we’re only seeing a few (some might say brave, others might say crazy) organizations using automation 100% of the time to push minor and major changes into production, a majority are using automation at least partially right now. That use will continue to expand as digital transformation puts pressure on IT to scale at a rate that can only be matched by automation.
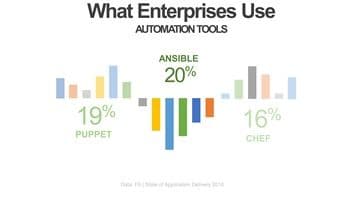
That means network operations has to get in the automation game, using the tools of the trade. Those tools are primarily Ansible, Puppet, and Chef according to our latest State of Application Delivery report.
But before NetOps can do that, it behooves those of us who provide the network and application services needed (and often required) to deliver apps safely at scale to support those toolsets.
And that’s the reason for this post today. F5 has been supporting NetOps need to move forward with automation by providing Ansible modules for quite some time now. The release of Ansible 2.5 is no exception, and we’re pleased to note that we’ve both enhanced existing F5 modules as well as added new ones to expand support for security (and maybe even get SecOps into the automation game).
If you aren’t familiar with automating with Ansible, here’s the thirty second pitch: Ansible is an open source, agentless engine that automates the configuration of one or more hosts as described by directives in a playbook.
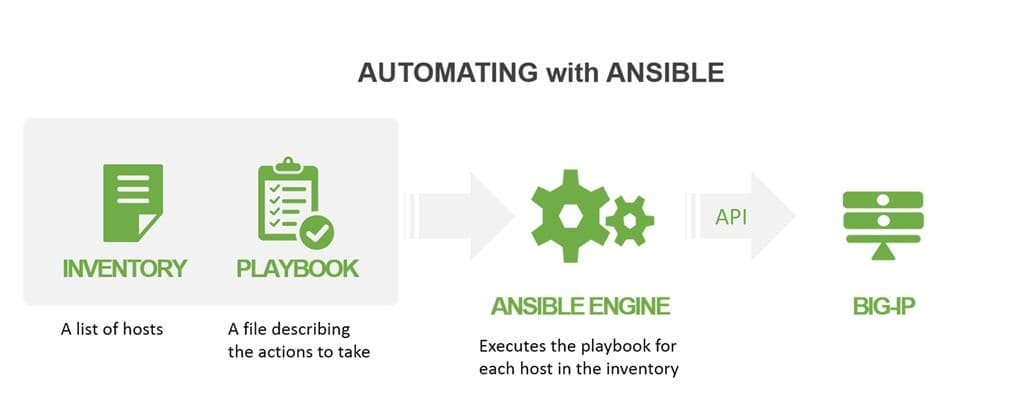
It’s a declarative model, meaning the playbook describes actions and provides values (like host names or IP addresses or specific settings like a load balancing algorithm) and nothing else. Ansible modules are tasked with reading the playbook and executing commands to achieve the desired result. The Ansible engine can be run on a desktop, a laptop, or a server.
It’s extremely well-suited for organizations adopting an infrastructure as code approach to deployments, and insulates users from changes to modules over time. So even if something radically changes regarding BIG-IP that requires an update to the Ansible module, it shouldn’t affect existing playbooks. You can read more about BIG-IP and Ansible on DevCentral as well as find playbook examples and help using both.
Whether you’re just getting started or an Ansible pro, you’ll want to know what’s new in Ansible 2.5 with respect to BIG-IP. I’ve got your back there. We’ve added modules to support high-availability, BIG-IP ASM profiles, BIG-IP AFM policies, and iApp LX support among others. That’s in addition to existing modules covering a wide range of load balancing and security capabilities available with BIG-IP. The full list with clicky links is below the fold.
Ansible is amongst the most popular tools for network and application service automation. We’re excited to be a part of the Ansible community and support NetOps making the move to a more automated, software-driven deployment model with DevOps.
Automate all the things!
Here’s a partial list of what’s new in Ansible 2.5:
Ansible Module | Description |
Manages the AFM address lists on a BIG-IP | |
Manages the AFM port lists on a BIG-IP | |
Import ASM policies from file or existing template | |
Manages licenses in a BIG-IQ registration key pool | |
Manages registration key pools on BIG-IQ | |
BIG-IP HA Pairing | |
Deploys iApps LX packages to the BIG-IP | |
Manages LTM policy rules on a BIG-IP | |
Manages F5 BIG-IP LTM UDP monitors | |
Manages F5 BIG-IP LTM HTTPS monitors | |
Manages traffic groups on BIG-IP | |
Manages vCMP guests on a BIG-IP | |
Manages client SSL profiles on a BIG-IP |
About the Author

Related Blog Posts

Why sub-optimal application delivery architecture costs more than you think
Discover the hidden performance, security, and operational costs of sub‑optimal application delivery—and how modern architectures address them.

Keyfactor + F5: Integrating digital trust in the F5 platform
By integrating digital trust solutions into F5 ADSP, Keyfactor and F5 redefine how organizations protect and deliver digital services at enterprise scale.

Architecting for AI: Secure, scalable, multicloud
Operationalize AI-era multicloud with F5 and Equinix. Explore scalable solutions for secure data flows, uniform policies, and governance across dynamic cloud environments.

Nutanix and F5 expand successful partnership to Kubernetes
Nutanix and F5 have a shared vision of simplifying IT management. The two are joining forces for a Kubernetes service that is backed by F5 NGINX Plus.

AppViewX + F5: Automating and orchestrating app delivery
As an F5 ADSP Select partner, AppViewX works with F5 to deliver a centralized orchestration solution to manage app services across distributed environments.
F5 NGINX Gateway Fabric is a certified solution for Red Hat OpenShift
F5 collaborates with Red Hat to deliver a solution that combines the high-performance app delivery of F5 NGINX with Red Hat OpenShift’s enterprise Kubernetes capabilities.
