Delivering Zero Trust with Microsoft Azure Active Directory’s Conditional Access and BIG-IP APM
Even before the pandemic, many employees were already accessing applications and data resources from home, coffee shops, and on the road using corporate-issued or personal devices. Today, many organizations are empowering their employees to work from anywhere (WFA) to alleviate commute times, provide work-life balance, and enable them to reside anywhere geographically. Organizations embrace WFA because it saves costs by consolidating or even closing some physical locations. Plus, they now recognize that their employees can be productive from anywhere.
While there are certainly benefits to WFA, the trend increases the pressure on companies to enable the strictest security measures on remote user access while ensuring a seamless user experience for application and data access. Also, applications and access to them will remain hybrid for some time, with some apps in the public cloud—such as native cloud or SaaS apps—and other apps on-premises, in a data center, or in a private cloud. This makes application access much more complex for users and organizations alike, and significantly more difficult to secure. It also puts more stress on organizations trying to deploy a Zero Trust architecture across all of their applications, regardless of where they reside.
Most mission-critical applications—like classic and custom applications—cannot be migrated to the cloud. Classic applications, such as those developed by Oracle and SAP, and custom apps typically don’t or can’t support modern authentication standards and protocols such as SAML and OIDC. Support for identity federation and single sign-on (SSO) is also often unavailable. Many cannot support multi-factor authentication (MFA), either. This means your organization must manage multiple points and methods of user authentication, while users must manage different credentials and various forms of authentication and access for different applications. This creates a complicated, confusing experience for employees and contractors, increasing workloads for your administrators, and rising IT support costs.
Organizations must enable simple, secure user access to all applications, regardless of where they are hosted. This helps improve user experience no matter where users are, while simultaneously making life easier for administrators.
BIG-IP Access Policy Manager (APM) is F5’s secure, highly-scalable access management proxy solution that enables centralized global access control for users, devices, applications, and APIs. Microsoft Azure Active Directory (AD) is Microsoft’s comprehensive cloud-based Identity and access management platform.
Working together, BIG-IP APM and Azure AD combine to enable seamless, secure access to all applications, regardless of where they’re hosted—in the public cloud, as native cloud or SaaS applications, on-premises, in a data center, or in a private cloud. The integrated solution simplifies application access for your employees, greatly improving their experience while significantly reducing application access security risks for your business. It allows employees to securely access all authorized applications, whether those applications support modern authentication standards and protocols or classic authentication methods, such as Kerberos or header-based methods.
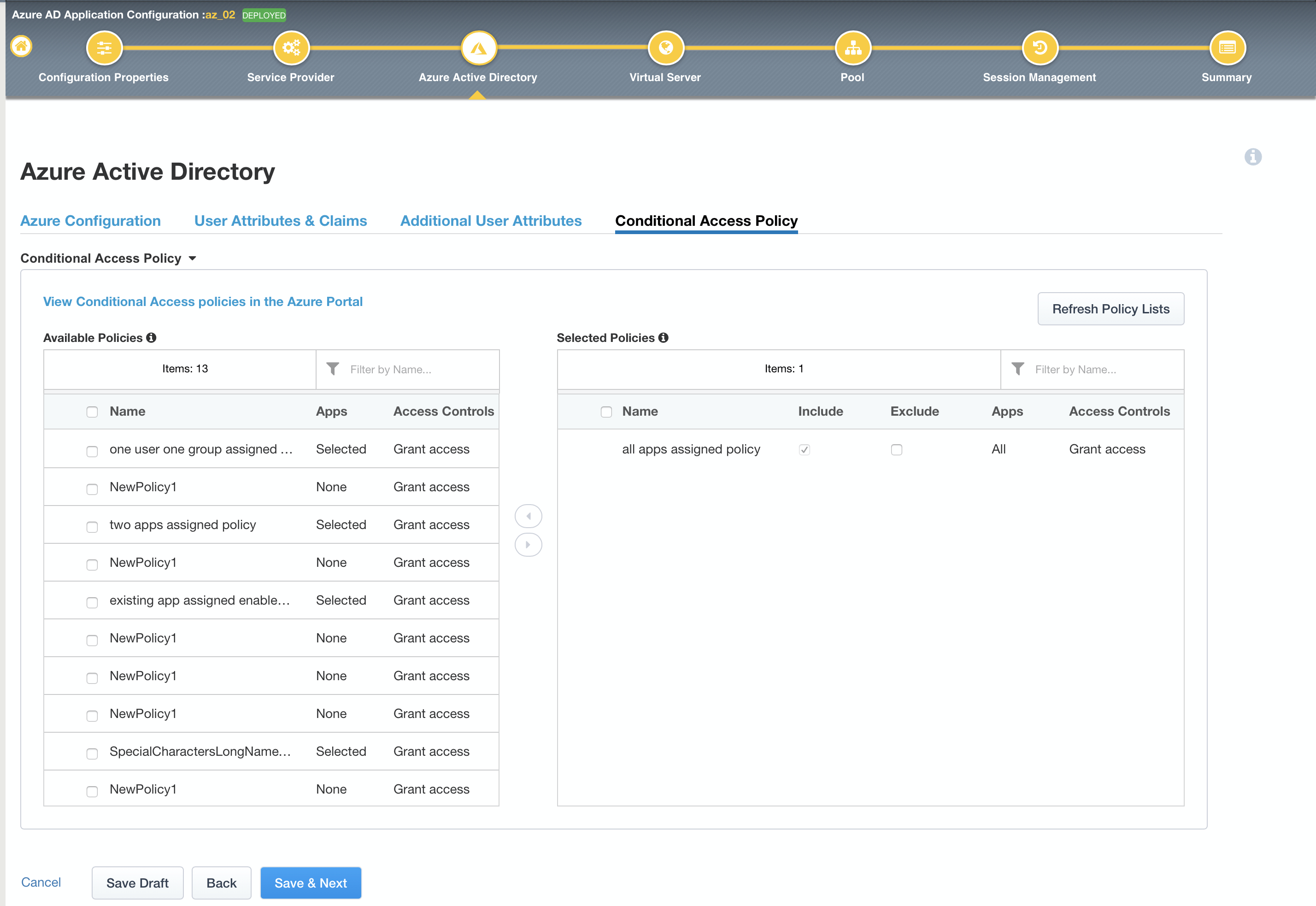
With the BIG-IP v16.1 release, BIG-IP APM and Microsoft Azure AD are extending application access security by integrating Azure AD Conditional Access functionality within the BIG-IP APM user interface.
Azure AD Conditional Access is a tool used by Azure AD to bring signals together, make decisions, and enforce organizational policies. Policies at their simplest are “if-then” statements: If a user wants to access a resource, then they must meet or comply with the policies set in place. By using Conditional Access policies, you can apply the right access controls when needed to keep your organization secure.
Common signals that Microsoft Azure AD Conditional Access can consider when making a policy decision include:
- User or group membership
- IP location information
- Device health
- Application type
- User and session risk
Then, based on those signals, a decision is made to either allow, grant, or block user access. Azure AD Conditional Access acts as the policy engine in which real-time evaluation occurs, working with BIG-IP APM for enforcement.
You can see the screenshot of this new experience below:
Through this new integration, BIG-IP APM and Azure AD:
- Leverage a single and easy to use interface for your apps: Through BIG-IP APM’s Access Guided Configuration (AGC), administrators can use a single interface to configure and manage policy control across all apps—including custom apps, and classic apps, such as Oracle E-Business Suite (EBS), Oracle JD Edwards, and SAP ERP—for an easy onboarding experience.
- Empower your users to be productive wherever and whenever: With the integration of Azure AD Conditional Access and BIG-IP APM, users can simply and seamlessly access cloud-based and custom/classic apps if they meet conditions set by their administrators.
- Centralize user authentication: Administrators don’t have to manage separate authentication methods for cloud-based apps and other methods for classic/custom applications.
- Protect your organization’s assets: By integrating Azure AD and BIG-IP APM, additional appropriate access controls may be applied when needed to keep apps and data secure. BIG-IP APM goes even further in providing protection by granting access to users on a per-app request basis.
F5 and Microsoft will continue to deliver a best-of-breed integrated solution for adopting and adapting Zero Trust across all of your applications, while F5 will keep providing administrators the tools to greatly ease access management and configuration for your apps.
You can find more details about the joint BIG-IP APM and Microsoft Azure AD solution here.