Financial Malware and its Tricks: Mobile Malware
Modern Banking with Mobile
Mobile devices are rapidly becoming the instrument of choice for digital users, impacting the financial sector as well. The new generation needs banking to be mobile-friendly. Per the findings of the Federal Reserve, mobile banking usage is at 67% for the age group of 18-to-29. The primary concern for not adopting mobile for banking was security. With mobility being an unstoppable force, organizations need to understand this risk vector to adequately plan for and mitigate threats. This article is directed toward some of the most notable (and exploited) vulnerabilities in the mobile space.
What is Mobile Malware?
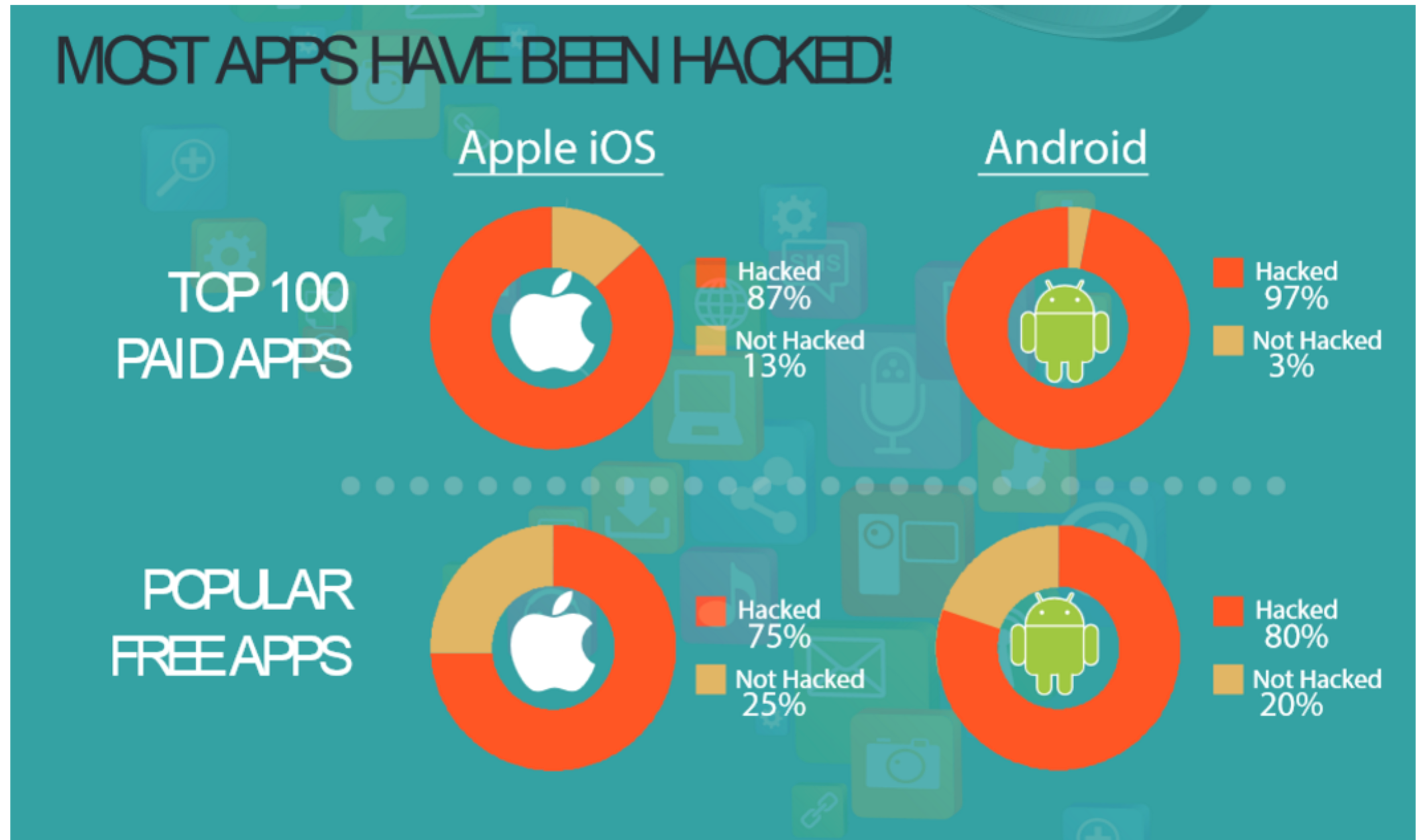
As with any malware, mobile malware is a piece of code written to attack a smart phone or similar device. Mobile malware history goes back to at least the year 2000, when the first know mobile malware “TIMOFONICA” was detected by researchers. In 2016, malware like "Godless" that can root up to 90% Android devices are found in the wild.
A quick look at the analytics done by Kaspersky lab shows the number of Mobile Banking Trojans is going up. About 56,194 users were attacked by mobile banking Trojans at least once during the year 2015.

Types: Spyware and Adware, Trojan and Viruses, Phishing Apps etc.
Malware active in the wild can be currently classified as spyware/adware, Trojan and viruses, phishing apps, or bot processes. Their sole intention is to capture valuable personal information and exfiltrate it.
- Spyware and adware disguised as a legitimate app are known to gather user and device information, which can be used for future attacks.
- Trojans hijack devices and send unauthorized premium text SMS. The more prevalent ones have the capability to redraw on user screens and act as legitimate applications to steal confidential information like banking credentials and out of band one-time passwords.
- Phishing Applications leverage rogue or refactored applications to deliver malicious content to the user.
Common Vulnerabilities and Tricks Utilized by Mobile Malware
Mobile devices support multiple platforms like iOS, Android, Windows, etc. With iOS and Android dominating the market, lets take a look at relevant vulnerabilities that are exploited:
- Rooted or Jailbroken Devices: Rooting/Jailbreaking a phone provides root level access to the mobile operating system. While this gives users the capability to modify the stock behavior of the device, this also creates an extreme risk to the applications as the process breaks the security model of the device. A rooted/jailbroken device provides perfect avenue for malware and rogue application to infect and exfiltrate data.
- Man in The Middle Attacks: This attack vector utilizes a third party coming in between the device and server communication, sniffing and altering the payload. With mobile devices, attack vectors are amplified as people tend to connect to free Wi-Fi zones at hotels, coffee shops, and other public places,
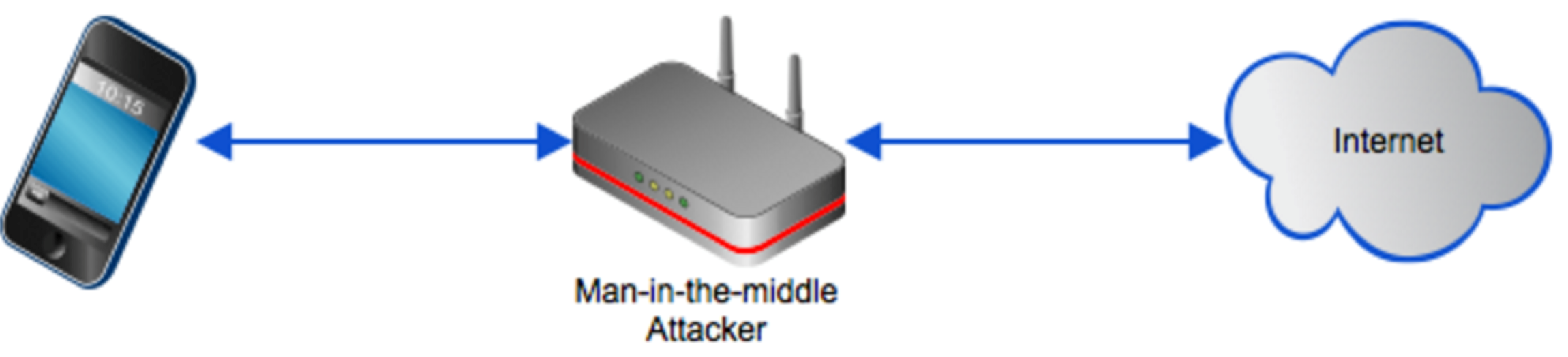
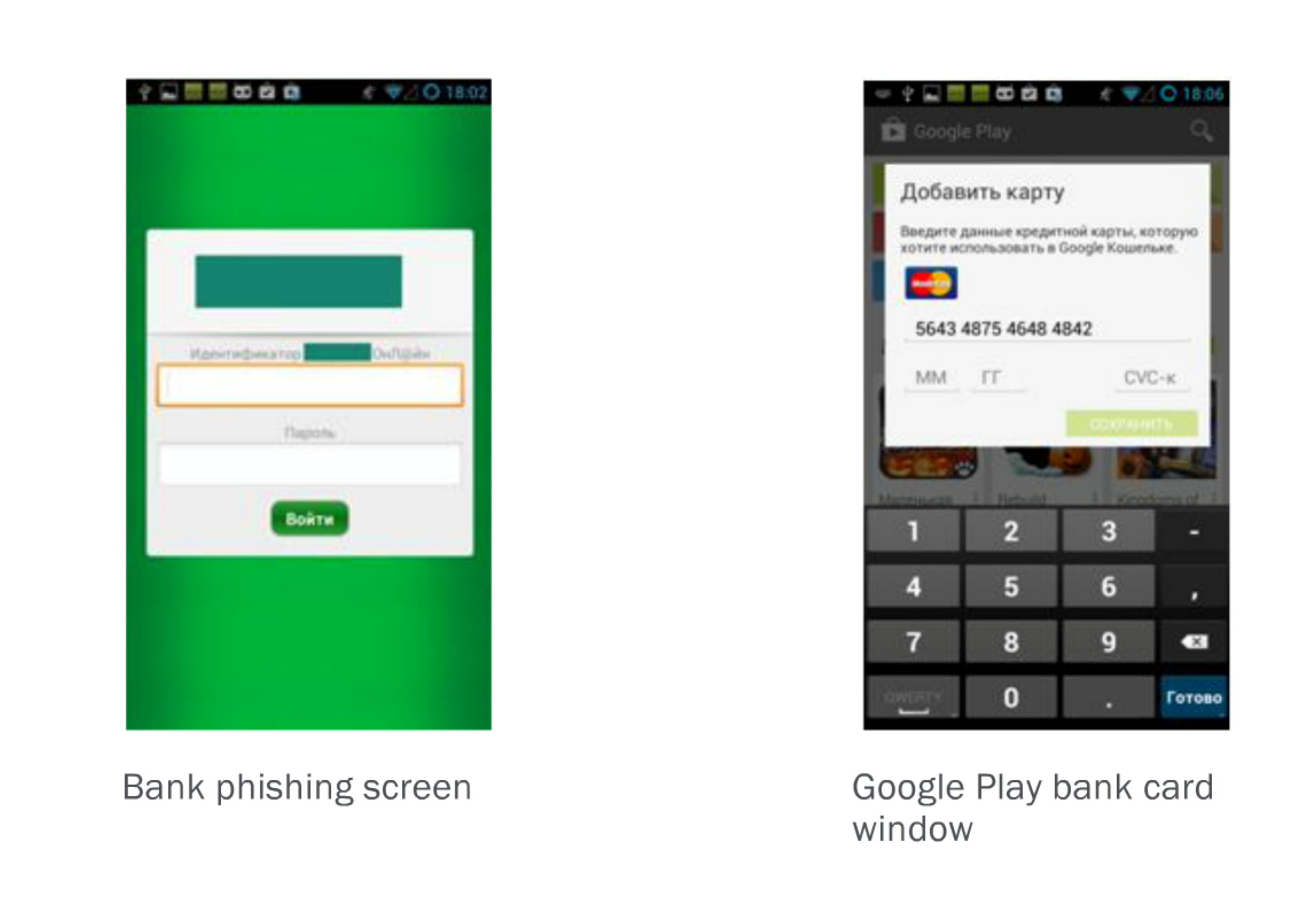
- Non Jailbroken iOS malware: New variants of malware (example: YiSpecter) have been detected which are able to infect iOS and abuse private APIs.
- And many more...Malware authors are relentlessly inventing and coming up with new techniques to compromise mobile devices.
F5’s Fraud Protection Solution is the Answer
Fraud protection provides organizations with preventive and detective mitigation approaches for modern mobile applications. A range of techniques is used to assess the security integrity of the device; this information is provided to the application and shared with an organization's risk engine to mitigate and remediate threats. Some key features that help overcome these threats include:
Certificate Forging Detection: Checking the certificate helps prevent against Man in The Middle attacks. The functionality checks for certificate validity against the stored information.
DNS Spoofing Detection: Defends against Man in the Middle attacks by resolving server names and comparing them against stored information.
Jailbreak/Rooting Detection: Detects compromised device by checking for root privileges.
Malware Detection: Looks for indicators of compromise and conducts behavior analysis to find installed malware on the device.
Unpatched/Unsecure OS detection: SDK is able to compute the Android Version/iOS version and provide the information to an application.
Focus Stealing Detection: The feature allows application to detect if a rogue application stole focus from the protected application. MobileSafe will generate a broadcast event for the application to respond to this threat.
Repackaging Detection: For Android apps, the solution will check for the signature to ascertain its authenticity, For iOS, checking for repackaging involves computing MD5 hashes and validating.
Setting Up the Environment
The solution can be set up by enabling F5 MobileSafe on an existing WebSafe environment.
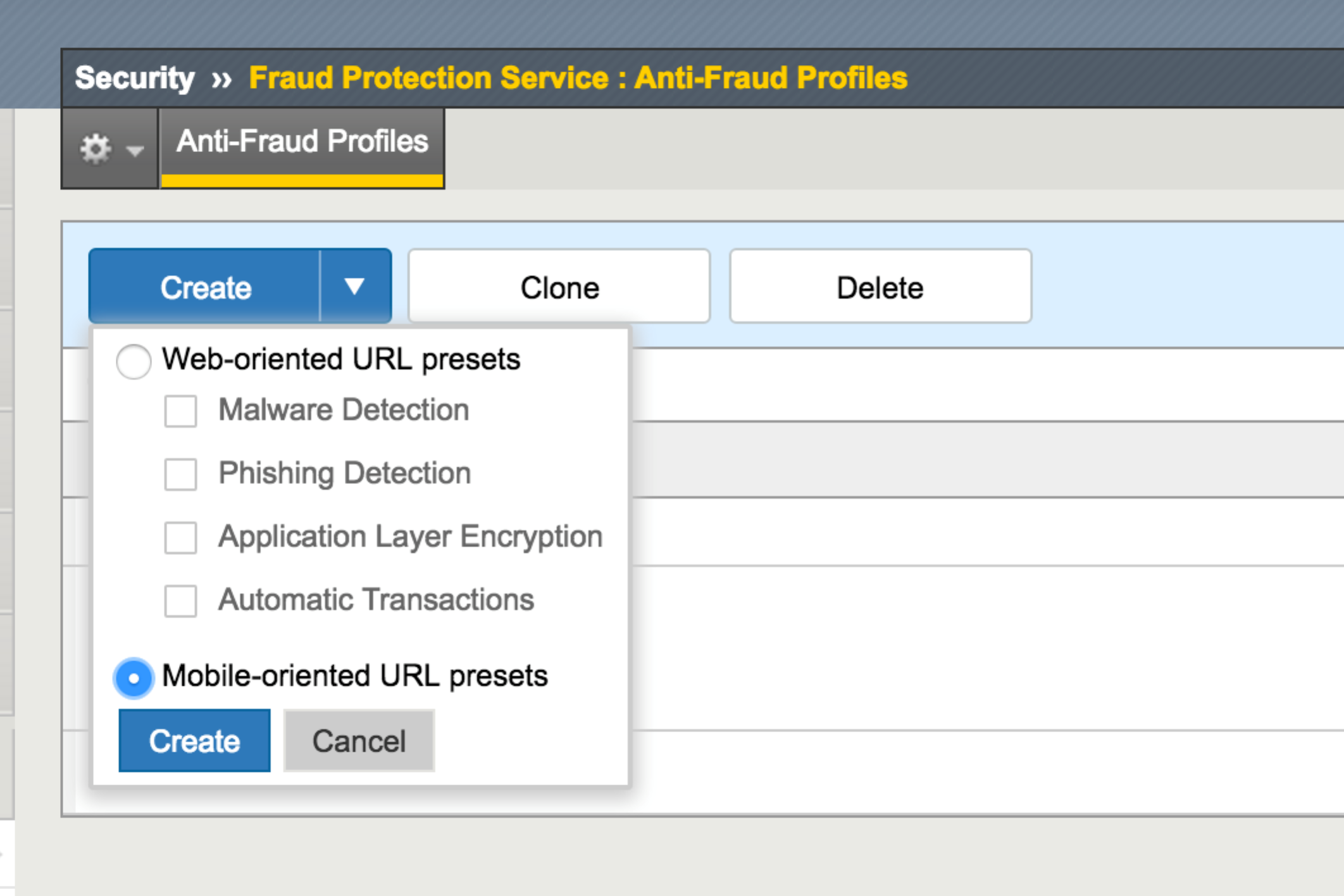
- Once the profile is created, alerts will be available on Alert Server when a user accesses the mobile URLs.
Conclusion
Mobile devices provide users with convenient and easy access to online services, fuelling massive adoption. Hackers are trying to maximize new attack vectors because of the limited understanding of security in this domain. F5’s Fraud Protection Solution provides organization a view into the mobile endpoints and protects against modern and sophisticated threats.
Resources
- F5 Anti-Fraud Solution: https://f5.com/products/modules/websafe
- Mobile Man in the Middle Attack: http://www.information-age.com/technology/security/123461071/what-are-mobile-man-middle-attacks-and-how-dangerous-are-they
